updates
This commit is contained in:
@@ -31,7 +31,7 @@ Domain names for the application/human layer
|
|||||||
|
|
||||||
- E.g., www.wustl.edu
|
- E.g., www.wustl.edu
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|||||||
27
content/CSE4303/CSE4303_L4.md
Normal file
27
content/CSE4303/CSE4303_L4.md
Normal file
@@ -0,0 +1,27 @@
|
|||||||
|
# CSE4303 Introduction to Computer Security (Lecture 4)
|
||||||
|
|
||||||
|
## Network attacks
|
||||||
|
|
||||||
|
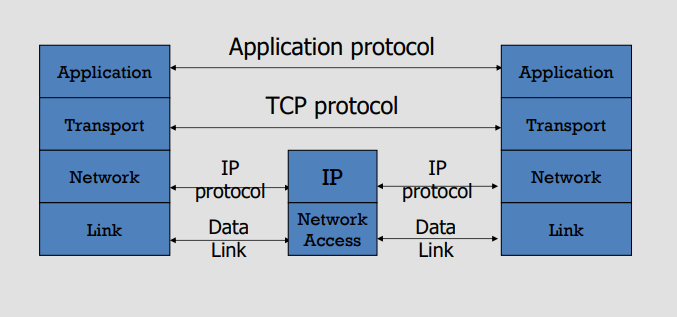
### Examining the transport layer
|
||||||
|
|
||||||
|
#### Transmission Control Protocol (TCP)
|
||||||
|
|
||||||
|
Connection-oriented, preserves order
|
||||||
|
|
||||||
|
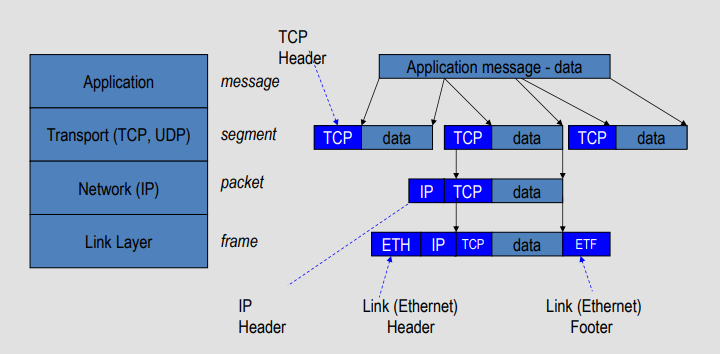
- Sender
|
||||||
|
- Break data into packets
|
||||||
|
- Attach packet numbers
|
||||||
|
- Receiver
|
||||||
|
- Acknowledge receipt; lost packets are resent
|
||||||
|
- Reassemble packets in correct order
|
||||||
|
|
||||||
|
#### Security Problems
|
||||||
|
|
||||||
|
1. Network packets pass by untrusted hosts
|
||||||
|
- Eavesdropping, packet sniffing
|
||||||
|
- Especially easy when attacker controls a machine close to victim (e.g. WiFi routers)
|
||||||
|
2. TCP state easily obtained by eavesdropping
|
||||||
|
- Enables spoofing and session hijacking
|
||||||
|
3. Denial of Service (DoS) vulnerabilities
|
||||||
|
|
||||||
|
|
||||||
@@ -6,4 +6,6 @@ export default {
|
|||||||
CSE4303_L1: "Introduction to Computer Security (Lecture 1)",
|
CSE4303_L1: "Introduction to Computer Security (Lecture 1)",
|
||||||
CSE4303_L2: "Introduction to Computer Security (Lecture 2)",
|
CSE4303_L2: "Introduction to Computer Security (Lecture 2)",
|
||||||
CSE4303_L3: "Introduction to Computer Security (Lecture 3)",
|
CSE4303_L3: "Introduction to Computer Security (Lecture 3)",
|
||||||
|
CSE4303_L4: "Introduction to Computer Security (Lecture 4)",
|
||||||
|
|
||||||
}
|
}
|
||||||
|
|||||||
Reference in New Issue
Block a user