Compare commits
31 Commits
b901998192
...
main
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
c4888b796c | ||
|
|
a7ef223f67 | ||
|
|
005cd7dbd6 | ||
|
|
ef9059d27c | ||
|
|
bdf0ff9f06 | ||
|
|
669e1c889a | ||
|
|
b6b80f619a | ||
|
|
2529a251e7 | ||
|
|
5b103812b4 | ||
|
|
16f09e5723 | ||
|
|
83ada2df2a | ||
|
|
8f2e613b36 | ||
|
|
e69362ce3c | ||
|
|
6a0b35bb28 | ||
|
|
778538cce0 | ||
|
|
f3c54c4dc7 | ||
|
|
a861477d74 | ||
|
|
c51226328c | ||
|
|
ba9aedfc5a | ||
|
|
bce2fa426c | ||
|
|
52e69f9340 | ||
|
|
eead5b6458 | ||
|
|
0161388082 | ||
|
|
90b2f582cc | ||
|
|
0c526a4983 | ||
|
|
05602ed70d | ||
|
|
838536bd1e | ||
|
|
b57c9e2f8d | ||
|
|
07486be083 | ||
|
|
a4d7024884 | ||
|
|
d6502a8737 |
131
content/CSE4303/CSE4303_L3.md
Normal file
131
content/CSE4303/CSE4303_L3.md
Normal file
@@ -0,0 +1,131 @@
|
||||
# CSE4303 Introduction to Computer Security (Lecture 3)
|
||||
|
||||
## Network attacks
|
||||
|
||||
### Internet Infrastructures
|
||||
|
||||
Local and interdomain routing
|
||||
|
||||
- TCP/IP for routing and messaging
|
||||
- BGP for routing announcements
|
||||
|
||||
Domain Name System
|
||||
|
||||
- Find IP address from symbolic name (cse.wustl.edu)
|
||||
|
||||
Media Access Control (MAC) addresses in the network access layer
|
||||
|
||||
- Associated w/ network interface card (NIC)
|
||||
- 00-50-56-C0-00-01
|
||||
|
||||
IP addresses for the network layer
|
||||
|
||||
- IPv4(32 bit) vs IPv6(128 bit)
|
||||
- 128.1.1.3 vs fe80::fc38:6673:f04d:b37b%4
|
||||
|
||||
IP addresses + ports for the transport layer
|
||||
|
||||
- E.g., 10.0.0.2:8080
|
||||
|
||||
Domain names for the application/human layer
|
||||
|
||||
- E.g., www.wustl.edu
|
||||
|
||||
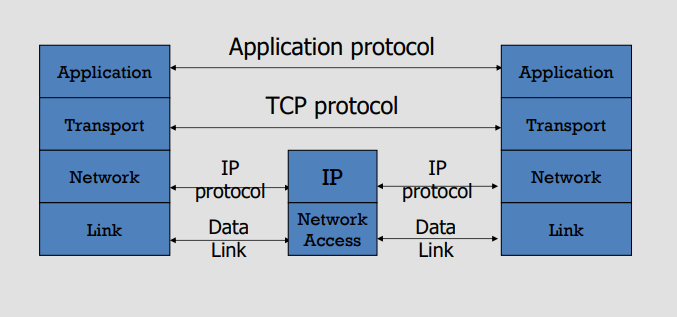
|
||||
|
||||
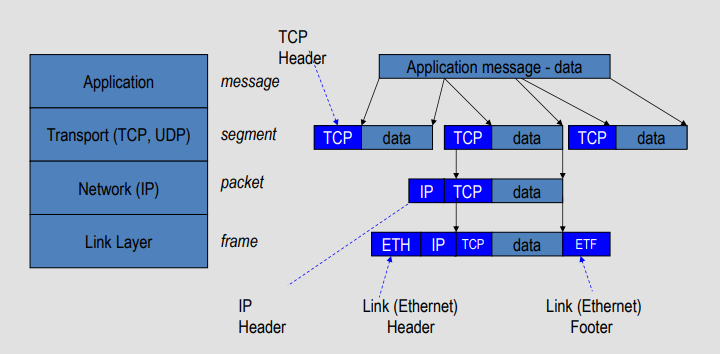
|
||||
|
||||
### Wireshark
|
||||
|
||||
Wireshark is a packet sniffer and protocol analyzer
|
||||
|
||||
- Captures and analyzes frames
|
||||
- Supports plugins
|
||||
|
||||
Usually required to run with administrator privileges
|
||||
|
||||
Setting the network interface in promiscuous mode captures traffic across the entire LAN segment and not just frames addressed to the machine
|
||||
|
||||
### Examining the link layer
|
||||
|
||||
When a packet arrives at the destination subnet, MAC address is used to deliver the packet
|
||||
|
||||
#### ARP: Address Resolution Protocol
|
||||
|
||||
- Each IP node (Host, Router) on LAN has ARP table
|
||||
- ARP Table: IP/MAC address mappings for some LAN nodes
|
||||
`< IP address; MAC address; TTL>`
|
||||
- TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min)
|
||||
|
||||
#### Lack of Source Authentication - ARP Spoofing (ARP Poisoning)
|
||||
|
||||
Send fake or 'spoofed', ARP messages to an Ethernet LAN.
|
||||
|
||||
- To have other machines associate IP addresses with the attacker’s MAC
|
||||
|
||||
Legitimate use
|
||||
|
||||
- Implementing redundancy and fault tolerance
|
||||
|
||||
#### ARP Poisoning (Spoofing) Defense
|
||||
|
||||
Prevention
|
||||
|
||||
- Static ARP table
|
||||
- DHCP Certification (use access control to ensure that hosts only use the IP addresses assigned to them, and that only authorized DHCP servers are accessible).
|
||||
|
||||
Detection
|
||||
|
||||
- Arpwatch (sending email when updates occur)
|
||||
|
||||
### Examining the network layer
|
||||
|
||||
Internet Protocol (IP)
|
||||
|
||||
Connectionless
|
||||
|
||||
- Unreliable
|
||||
- Best effort
|
||||
|
||||
Notes:
|
||||
|
||||
- src and dest ports not parts of IP hdr
|
||||
|
||||
#### IP Protocol Functions (Summary)
|
||||
|
||||
Routing
|
||||
|
||||
- IP host knows location of router (gateway)
|
||||
- IP gateway must know route to other networks
|
||||
|
||||
Fragmentation and reassembly
|
||||
|
||||
- If max-packet-size less than the user-data-size
|
||||
|
||||
Error reporting
|
||||
|
||||
- ICMP packet to source if packet is dropped
|
||||
|
||||
TTL field: decremented after every hop
|
||||
|
||||
- Packet dropped if TTL=0. Prevents infinite loops
|
||||
|
||||
#### Problem: no src IP authentication
|
||||
|
||||
Client is trusted to embed correct source IP
|
||||
|
||||
- Easy to override using raw sockets
|
||||
|
||||
- Libnet: a library for formatting raw packets with arbitrary IP headers
|
||||
|
||||
- Scapy: a python library for packet crafting
|
||||
|
||||
Anyone who owns their machine can send packets with arbitrary source IP
|
||||
|
||||
- ... response will be sent back to forged source IP
|
||||
|
||||
Implications:
|
||||
|
||||
- Anonymous DoS attacks;
|
||||
- Anonymous infection attacks (e.g. slammer worm)
|
||||
|
||||
142
content/CSE4303/CSE4303_L4.md
Normal file
142
content/CSE4303/CSE4303_L4.md
Normal file
@@ -0,0 +1,142 @@
|
||||
# CSE4303 Introduction to Computer Security (Lecture 4)
|
||||
|
||||
## Network attacks
|
||||
|
||||
### Examining the transport layer
|
||||
|
||||
#### Transmission Control Protocol (TCP)
|
||||
|
||||
Connection-oriented, preserves order
|
||||
|
||||
- Sender
|
||||
- Break data into packets
|
||||
- Attach packet numbers
|
||||
- Receiver
|
||||
- Acknowledge receipt; lost packets are resent
|
||||
- Reassemble packets in correct order
|
||||
|
||||
#### Security Problems
|
||||
|
||||
1. Network packets pass by untrusted hosts
|
||||
- Eavesdropping, packet sniffing
|
||||
- Especially easy when attacker controls a machine close to victim (e.g. WiFi routers)
|
||||
2. TCP state easily obtained by eavesdropping
|
||||
- Enables spoofing and session hijacking
|
||||
3. Denial of Service (DoS) vulnerabilities
|
||||
|
||||
#### TCP SYN Flood I: low rate (DoS Bug)
|
||||
|
||||
Low rate SYN flood defenses
|
||||
|
||||
Correct Solution:
|
||||
|
||||
Syncookies: remove state from server
|
||||
|
||||
Small performance overhead
|
||||
|
||||
Hijacking Existing TCP connection
|
||||
|
||||
- A, B trusted connection
|
||||
- Send packets with predictable seq numbers
|
||||
|
||||
- E impersonates B to A
|
||||
- DoS B’s queue
|
||||
- Sends packets to A that
|
||||
resemble B’s transmission
|
||||
- E cannot receive, but may
|
||||
execute commands on A
|
||||
|
||||
## Routing Security
|
||||
|
||||
Routing Protocols
|
||||
|
||||
- ARP (addr resolution protocol): IP addr ⟶ eth addr
|
||||
Security issues: (local network attacks)
|
||||
- Node A can confuse gateway into sending it traffic for Node B
|
||||
- By proxying traffic, node A can read/inject packets
|
||||
into B’s session (e.g. WiFi networks)
|
||||
- OSPF: used for routing within an AS
|
||||
- BGP: routing between Autonomous Systems
|
||||
Security issues: unauthenticated route updates
|
||||
- Anyone can cause entire Internet to send traffic
|
||||
for a victim IP to attacker’s address
|
||||
- Example: Youtube-Pakistan mishap (see DDoS lecture)
|
||||
- Anyone can hijack route to victim
|
||||
|
||||
### Security Issues
|
||||
|
||||
- BGP path attestations are un-authenticated
|
||||
- Anyone can inject advertisements for arbitrary routes
|
||||
- Advertisement will propagate everywhere
|
||||
- Used for DoS, spam, and eavesdropping (details in DDoS lecture)
|
||||
- Often a result of human error
|
||||
|
||||
Solutions:
|
||||
|
||||
- RPKI: AS obtains a certificate (ROA) from regional authority (RIR) and attaches ROA to path advertisement.
|
||||
Advertisements without a valid ROA are ignored. Defends against a malicious AS
|
||||
- SBGP: sign every hop of a path advertisement
|
||||
|
||||
### Domain Name System
|
||||
|
||||
DNS Root Name Servers
|
||||
|
||||
- Hierarchical service
|
||||
- Root name servers for toplevel domains
|
||||
- Authoritative name servers
|
||||
for subdomains
|
||||
- Local name resolvers contact
|
||||
authoritative servers when
|
||||
they do not know a name
|
||||
|
||||
#### DNS Lookup Example
|
||||
|
||||
#### Caching
|
||||
|
||||
- DNS responses are cached
|
||||
- Quick response for repeated translations
|
||||
- Note: NS records for domains also cached
|
||||
- DNS negative queries are cached
|
||||
- Save time for nonexistent sites, e.g. misspelling
|
||||
- Cached data periodically times out
|
||||
- Lifetime (TTL) of data controlled by owner of data
|
||||
- TTL passed with every record
|
||||
|
||||
DNS Packet
|
||||
|
||||
- Query ID:
|
||||
- 16 bit random value
|
||||
- Links response to query
|
||||
|
||||
#### Basic DNS Vulnerabilities
|
||||
|
||||
- Users/hosts trust the host-address mapping
|
||||
provided by DNS:
|
||||
- Used as basis for many security policies:
|
||||
Browser same origin policy, URL address bar
|
||||
- Obvious problems
|
||||
- Interception of requests or compromise of DNS servers can
|
||||
result in incorrect or malicious responses
|
||||
- e.g.: malicious access point in a Cafe
|
||||
- Solution - authenticated requests/responses
|
||||
- Provided by DNSsec … but few use DNSsec
|
||||
|
||||
### DNS cache poisoning (a la Kaminsky’08)
|
||||
|
||||

|
||||
|
||||
#### DNS poisoning attacks in the wild
|
||||
|
||||
- January 2005, the domain name for a large New York ISP, Panix, was hijacked to a site in Australia.
|
||||
- In November 2004, Google and Amazon users were sent to Med Network Inc., an online pharmacy
|
||||
- In March 2003, a group dubbed the "Freedom Cyber Force Militia" hijacked visitors to the Al-Jazeera Web site and presented them with the message "God Bless Our Troops"
|
||||
|
||||
### Summary
|
||||
|
||||
- Core protocols not designed for security
|
||||
- Eavesdropping, Packet injection, Route stealing, DNS poisoning
|
||||
- Patched over time to prevent basic attacks
|
||||
- More secure variants exist :
|
||||
- IP $\to$ IPsec
|
||||
- DNS $\to$ DNSsec
|
||||
- BGP $\to$ sBGPs
|
||||
79
content/CSE4303/CSE4303_L5.md
Normal file
79
content/CSE4303/CSE4303_L5.md
Normal file
@@ -0,0 +1,79 @@
|
||||
# CSE4303 Introduction to Computer Security (Lecture 5)
|
||||
|
||||
## Cryptography: Foundations
|
||||
|
||||
### Definitions
|
||||
|
||||
Cryptography is the study of techniques that enable secure communication and computation in the presence of adversaries, by providing formal guarantees such as confidentiality, integrity, and authenticity.
|
||||
|
||||
Cryptanalysis is the study of techniques for breaking cryptographic systems, by recovering secret information or violating security guarantees without knowing the secret key
|
||||
|
||||
### Background: security guarantee
|
||||
|
||||
- Well-defined statement about difficulty of compromising a system
|
||||
- ...with clear implicit or explicit assumptions about:
|
||||
- Parameters of the system
|
||||
- Threat model
|
||||
- Attack surfaces
|
||||
- Example: "A one-time pad cipher is secure against any cryptanalysis, including a brute-force attack, assuming:
|
||||
- the key is the same length as the plaintext,
|
||||
- the key is truly random, and
|
||||
- the key is never re-used.
|
||||
- Example: "Given that keys remain uncompromised (by human error, side channel, etc.), recovering an RSA private key from a given public key is at least as hard as integer factorization."
|
||||
- I.e. we can reduce RSA to integer factorization.
|
||||
- Note: correct implementation is not guaranteed!
|
||||
- Non-example: "This app is secure."
|
||||
- Empty claim: what does it mean?
|
||||
|
||||
### Overview: Encryption and Decryption
|
||||
|
||||
- The message m is called the plaintext.
|
||||
- Alice will convert plaintext m to an encrypted form using an encryption algorithm E that outputs a ciphertext c for m
|
||||
|
||||
#### Cryptography goals
|
||||
|
||||
- Confidentiality:
|
||||
- Mallory and Eve cannot recover original message from ciphertext
|
||||
- Integrity:
|
||||
- Mallory cannot modify message from Alice to Bob without detection
|
||||
by Bob
|
||||
- Authenticity:
|
||||
- Mallory cannot craft a message that Bob would accept as coming from Alice
|
||||
|
||||
#### Cryptosystem compoents
|
||||
|
||||
1. The set of possible plaintexts (M)
|
||||
2. The set of possible ciphertexts (C)
|
||||
3. The set of encryption keys (K)
|
||||
4. The set of decryption keys (usually K as well)
|
||||
5. The correspondence between encryption keys and decryption
|
||||
keys
|
||||
6. The encryption algorithm to use (E)
|
||||
7. The decryption algorithm to use (D)
|
||||
|
||||
#### Symmetric ciphers:
|
||||
|
||||
A cipher defined over $(K,M,C)$ is a pair of efficient algorithms $(E,D)$ where $E: K\times M\to C$ and $D: K\times C \to M$
|
||||
|
||||
Correctness Property:
|
||||
|
||||
$\forall m\in M, \exists k\in K$, $E(k,m) = c\in C$, and $D(k,c) = m$
|
||||
|
||||
- $D$ and $E$ are often efficient (polynomial time | concrete time)
|
||||
- $E$ is encryption, often randomized.
|
||||
- $D$ is decryption, always deterministic.
|
||||
|
||||
#### Threat models
|
||||
|
||||
Attackers may have:
|
||||
|
||||
- collection of ciphertexts (ciphertext-only attack)
|
||||
- collection of plaintext/ciphertext pairs (known plaintext attack: KPA )
|
||||
- collection of plaintext/ciphertext pairs for plaintexts selected by the attacker (chosen plaintext attack: CPA )
|
||||
- collection of plaintext/ciphertext pairs for ciphertexts selected by the attacker (chosen ciphertext attack: CCA/CCA2 )
|
||||
|
||||
### Symmetric (shared-key) encryption
|
||||
|
||||
Refer to this lecture notes
|
||||
|
||||
[CSE442T Lecture 1](https://notenextra.trance-0.com/CSE442T/CSE442T_L1/)
|
||||
5
content/CSE4303/CSE4303_L6.md
Normal file
5
content/CSE4303/CSE4303_L6.md
Normal file
@@ -0,0 +1,5 @@
|
||||
# CSE4303 Introduction to Computer Security (Lecture 6)
|
||||
|
||||
Refer to this lecture notes
|
||||
|
||||
[CSE442T Lecture 3](https://notenextra.trance-0.com/CSE442T/CSE442T_L3/)
|
||||
65
content/CSE4303/CSE4303_L7.md
Normal file
65
content/CSE4303/CSE4303_L7.md
Normal file
@@ -0,0 +1,65 @@
|
||||
# CSE4303 Introduction to Computer Security (Lecture 7)
|
||||
|
||||
## Cyptography in Symmetric Systems
|
||||
|
||||
### Symmetric systems
|
||||
|
||||
Symmetric (shared-key) encryption
|
||||
|
||||
- Classical techniques
|
||||
- Computer-aided techniques
|
||||
- Formal reasoning
|
||||
- Realizations:
|
||||
- Stream ciphers
|
||||
- Block ciphers
|
||||
|
||||
#### Stream ciphers
|
||||
|
||||
1. Operate on PT one bit at a time (usually), as a bit "stream"
|
||||
2. Generate arbitrarily long keystream on demand
|
||||
|
||||
Security abstraction:
|
||||
|
||||
1. XOR transfers randomness of keystream to randomness of CT regardless of PT’s content
|
||||
2. Security depends on G being “practically” indistinguishable from random string and “practically” unpredictable
|
||||
3. Idea: shouldn’t be able to predict next bit of generator given all bits seen so far
|
||||
|
||||
Keystream $G(k)$
|
||||
|
||||
- Idea: shouldn’t be able to predict next bit of generator given all bits seen so far
|
||||
- Strategies and challenges: many!
|
||||
- Idea that doesn’t quite work: Linear Feedback Shift Register (LFSR)
|
||||
- Choice of feedback: by algebra
|
||||
- Pro: fast, statistically close to random
|
||||
- Problem: susceptible to cryptanalysis (b/c linear)
|
||||
- LFSR-based
|
||||
- Modifications to basic LFSR:
|
||||
- Use non-linear combo of multiple LFSRs
|
||||
- Use controlled clocking (e.g. only cycle the LFSR when another LFSR outputs a 1)
|
||||
- Etc.
|
||||
- Others: mod arithmetic-based, other algebraic constructions
|
||||
|
||||
#### Block ciphers
|
||||
|
||||
1. Operate on PT one block at a time
|
||||
2. Use same key for multiple blocks (with caveats)
|
||||
3. Chaining modes intertwine successive blocks of CT (or not)
|
||||
|
||||
View cipher as a Pseudo-Random Permutation (PRP)
|
||||
|
||||
- PRP defined over $(K, X)$:
|
||||
|
||||
$$
|
||||
E: K \times X \to X
|
||||
$$
|
||||
|
||||
such that:
|
||||
|
||||
1. There exists an “efficient” deterministic algorithm to evaluate $E(k,x)$.
|
||||
2. The function $E( k, \cdot )$ is one-to-one.
|
||||
3. There exists an “efficient” inversion algorithm $D(k,y)$.
|
||||
|
||||
- i.e. a PRF that is an invertible 1-to-1 mapping from message space to
|
||||
message space
|
||||
|
||||
|
||||
BIN
content/CSE4303/DNS_cache_poisoning.png
Normal file
BIN
content/CSE4303/DNS_cache_poisoning.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 105 KiB |
@@ -5,4 +5,9 @@ export default {
|
||||
},
|
||||
CSE4303_L1: "Introduction to Computer Security (Lecture 1)",
|
||||
CSE4303_L2: "Introduction to Computer Security (Lecture 2)",
|
||||
CSE4303_L3: "Introduction to Computer Security (Lecture 3)",
|
||||
CSE4303_L4: "Introduction to Computer Security (Lecture 4)",
|
||||
CSE4303_L5: "Introduction to Computer Security (Lecture 5)",
|
||||
CSE4303_L6: "Introduction to Computer Security (Lecture 6)",
|
||||
CSE4303_L7: "Introduction to Computer Security (Lecture 7)",
|
||||
}
|
||||
|
||||
@@ -32,241 +32,8 @@ Please refer to the syllabus for our policy regarding the use of GenAI.
|
||||
>
|
||||
> This notation system is annoying since in mathematics, $A^*$ is the transpose of $A$, but since we are using literatures in physics, we keep the notation of $A^*$. In this report, I will try to make the notation consistent as possible and follows the **physics** convention in this report. So every vector you see will be in $\ket{\psi}$ form. And we will avoid using the $\langle v,w\rangle$ notation for inner product as it used in math, we will use $\langle v|w\rangle$ or $\langle v,w\rangle$ to denote the inner product.
|
||||
|
||||
A quantum error-correcting code is defined to be a unitary mapping (encoding) of $k$ qubits (two-state quantum systems) into a subspace of the quantum state space of $n$ qubuits such that if any $t$ of the qubits undergo arbitary decoherence, not necessarily independently, the resulting $n$ qubit state can be used to faithfully reconstruct the original quantum state of the $k$ encoded qubits.
|
||||
|
||||
Asymptotic rate $k/n=1-2H_2(2t/n)$, where $H_2$ is the binary entropy function
|
||||
|
||||
$$
|
||||
H_2=-p\log_2(p)-(1-p)\log_2(1-p)
|
||||
$$
|
||||
|
||||
### Problem setting and motivation
|
||||
|
||||
#### Linear algebra 102
|
||||
|
||||
The main vector space we are interested in is $\mathbb{C}^n$, therefore, all the linear operator we defined are from $\mathbb{C}^n$ to $\mathbb{C}^n$.
|
||||
|
||||
We denote a vector in vector space as $\ket{\psi}=(z_1,\cdots,z_n)$ (might also be infinite dimensional, and $z_i\in\mathbb{C}$).
|
||||
|
||||
A natural inner product space defined on $\mathbb{C}^n$ is given by the Hermitian inner product:
|
||||
|
||||
$$
|
||||
\langle\psi|\varphi\rangle=\sum_{i=1}^n z_i\bar{z}_i
|
||||
$$
|
||||
|
||||
This satisfies the following properties:
|
||||
1. $\bra{\psi}\sum_i \lambda_i\ket{\varphi}=\sum_i \lambda_i \langle\psi|\varphi\rangle$ (linear on the second argument)
|
||||
2. $\langle\varphi|\psi\rangle=(\langle\psi|\varphi\rangle)^*$
|
||||
3. $\langle\psi|\psi\rangle\geq 0$ with equality if and only if $\ket{\psi}=0$
|
||||
|
||||
Here $\psi$ is just a label for the vector and you don't need to worry about it too much. This is also called the ket, where the counterpart:
|
||||
|
||||
- $\langle\psi\rangle$ is called the bra, used to denote the vector dual to $\psi$, such element is a linear functional if you really wants to know what that is.
|
||||
- $\langle\psi|\varphi\rangle$ is the inner product between two vectors, and $\bra{\psi} A\ket{\varphi}$ is the inner product between $A\ket{\varphi}$ and $\bra{\psi}$, or equivalently $A^\dagger \bra{\psi}$ and $\ket{\varphi}$.
|
||||
- Given a complex matrix $A=\mathbb{C}^{n\times n}$,
|
||||
- $A^*$ is the complex conjugate of $A$.
|
||||
- i.e., $A=\begin{bmatrix}1+i & 2+i & 3+i\\4+i & 5+i & 6+i\\7+i & 8+i & 9+i\end{bmatrix}$, $A^*=\begin{bmatrix}1-i & 2-i & 3-i\\4-i & 5-i & 6-i\\7-i & 8-i & 9-i\end{bmatrix}$
|
||||
- $A^\top$ is the transpose of $A$.
|
||||
- i.e., $A=\begin{bmatrix}1+i & 2+i & 3+i\\4+i & 5+i & 6+i\\7+i & 8+i & 9+i\end{bmatrix}$, $A^\top=\begin{bmatrix}1+i & 4+i & 7+i\\2+i & 5+i & 8+i\\3+i & 6+i & 9+i\end{bmatrix}$
|
||||
- $A^\dagger=(A^*)^\top$ is the complex conjugate transpose, referred to as the adjoint, or Hermitian conjugate of $A$.
|
||||
- i.e., $A=\begin{bmatrix}1+i & 2+i & 3+i\\4+i & 5+i & 6+i\\7+i & 8+i & 9+i\end{bmatrix}$, $A^\dagger=\begin{bmatrix}1-i & 4-i & 7-i\\2-i & 5-i & 8-i\\3-i & 6-i & 9-i\end{bmatrix}$
|
||||
- $A$ is unitary if $A^\dagger A=AA^\dagger=I$.
|
||||
- $A$ is hermitian (self-adjoint in mathematics literatures) if $A^\dagger=A$.
|
||||
|
||||
#### Motivation of Tensor product
|
||||
|
||||
Recall from the traditional notation of product space of two vector spaces $V$ and $W$, that is, $V\times W$, is the set of all ordered pairs $(\ket{v},\ket{w})$ where $\ket{v}\in V$ and $\ket{w}\in W$.
|
||||
|
||||
The space has dimension $\dim V+\dim W$.
|
||||
|
||||
We want to define a vector space with notation of multiplication of two vectors from different vector spaces.
|
||||
|
||||
That is
|
||||
|
||||
$$
|
||||
(\ket{v_1}+\ket{v_2})\otimes \ket{w}=(\ket{v_1}\otimes \ket{w})+(\ket{v_2}\otimes \ket{w})
|
||||
$$
|
||||
$$
|
||||
\ket{v}\otimes (\ket{w_1}+\ket{w_2})=(\ket{v}\otimes \ket{w_1})+(\ket{v}\otimes \ket{w_2})
|
||||
$$
|
||||
|
||||
and enables scalar multiplication by
|
||||
|
||||
$$
|
||||
\lambda (\ket{v}\otimes \ket{w})=(\lambda \ket{v})\otimes \ket{w}=\ket{v}\otimes (\lambda \ket{w})
|
||||
$$
|
||||
|
||||
And we wish to build a way associates the basis of $V$ and $W$ to the basis of $V\otimes W$. That makes the tensor product a vector space with dimension $\dim V\times \dim W$.
|
||||
|
||||
#### Definition of linear functional
|
||||
|
||||
> [!TIP]
|
||||
>
|
||||
> Note the difference between a linear functional and a linear map.
|
||||
>
|
||||
> A generalized linear map is a function $f:V\to W$ satisfying the condition
|
||||
>
|
||||
> 1. $f(\ket{u}+\ket{v})=f(\ket{u})+f(\ket{v})$
|
||||
> 2. $f(\lambda \ket{v})=\lambda f(\ket{v})$
|
||||
|
||||
A linear functional is a linear map from $V$ to $\mathbb{F}$.
|
||||
|
||||
#### Definition of bilinear functional
|
||||
|
||||
A bilinear functional is a bilinear function $\beta:V\times W\to \mathbb{F}$ satisfying the condition that $\ket{v}\to \beta(\ket{v},\ket{w})$ is a linear functional for all $\ket{w}\in W$ and $\ket{w}\to \beta(\ket{v},\ket{w})$ is a linear functional for all $\ket{v}\in V$.
|
||||
|
||||
The vector space of all bilinear functionals is denoted by $\mathcal{B}(V,W)$.
|
||||
|
||||
#### Definition of tensor product
|
||||
|
||||
Let $V,W$ be two vector spaces.
|
||||
|
||||
Let $V'$ and $W'$ be the dual spaces of $V$ and $W$, respectively, that is $V'=\{\psi:V\to \mathbb{F}\}$ and $W'=\{\phi:W\to \mathbb{F}\}$, $\psi, \phi$ are linear functionals.
|
||||
|
||||
The tensor product of vectors $v\in V$ and $w\in W$ is the bilinear functional defined by $\forall (\psi,\phi)\in V'\times W'$ given by the notation
|
||||
|
||||
$$
|
||||
(v\otimes w)(\psi,\phi)\coloneqq\psi(v)\phi(w)
|
||||
$$
|
||||
|
||||
The tensor product of two vector spaces $V$ and $W$ is the vector space $\mathcal{B}(V',W')$
|
||||
|
||||
Notice that the basis of such vector space is the linear combination of the basis of $V'$ and $W'$, that is, if $\{e_i\}$ is the basis of $V'$ and $\{f_j\}$ is the basis of $W'$, then $\{e_i\otimes f_j\}$ is the basis of $\mathcal{B}(V',W')$.
|
||||
|
||||
That is, every element of $\mathcal{B}(V',W')$ can be written as a linear combination of the basis.
|
||||
|
||||
Since $\{e_i\}$ and $\{f_j\}$ are bases of $V'$ and $W'$, respectively, then we can always find a set of linear functionals $\{\phi_i\}$ and $\{\psi_j\}$ such that $\phi_i(e_j)=\delta_{ij}$ and $\psi_j(f_i)=\delta_{ij}$.
|
||||
|
||||
Here $\delta_{ij}=\begin{cases}
|
||||
1 & \text{if } i=j \\
|
||||
0 & \text{otherwise}
|
||||
\end{cases}$ is the Kronecker delta.
|
||||
|
||||
$$
|
||||
V\otimes W=\left\{\sum_{i=1}^n \sum_{j=1}^m a_{ij} \phi_i(v)\psi_j(w): \phi_i\in V', \psi_j\in W'\right\}
|
||||
$$
|
||||
|
||||
Note that $\sum_{i=1}^n \sum_{j=1}^m a_{ij} \phi_i(v)\psi_j(w)$ is a bilinear functional that maps $V'\times W'$ to $\mathbb{F}$.
|
||||
|
||||
This enables basis free construction of vector spaces with proper multiplication and scalar multiplication.
|
||||
|
||||
This vector space is equipped with the unique inner product $\langle v\otimes w, u\otimes x\rangle_{V\otimes W}$ defined by
|
||||
|
||||
$$
|
||||
\langle v\otimes w, u\otimes x\rangle=\langle v,u\rangle_V\langle w,x\rangle_W
|
||||
$$
|
||||
|
||||
In practice, we ignore the subscript of the vector space and just write $\langle v\otimes w, u\otimes x\rangle=\langle v,u\rangle\langle w,x\rangle$.
|
||||
|
||||
> [!NOTE]
|
||||
>
|
||||
> All those definitions and proofs can be found in Linear Algebra Done Right by Sheldon Axler.
|
||||
|
||||
#### Definition of two-state quantum system
|
||||
|
||||
The finite dimensional Hilbert space $\mathcscr{H}
|
||||
|
||||
#### Definition of Coherent states from the view of physics
|
||||
|
||||
#### Side node: Why quantum error-correcting code is hard
|
||||
|
||||
Decoherence process
|
||||
|
||||
#### No-cloning theorem
|
||||
|
||||
> Reference from P.532 of the book
|
||||
|
||||
Suppose we have a quantum system with two slots $A$, and $B$, the data slot, starts out in an unknown but pure quantum state $\ket{\psi}$. This is the state which is to be copied into slot $B$m the target slot. We assume that the target slot starts out in some standard pure state $\ket{s}$. Thus the initial state of the copying machine is $\ket{\psi}\otimes \ket{s}$.
|
||||
|
||||
Assume there exists some unitary operator $U$ such that $U(\ket{\psi}\otimes \ket{s})=\ket{\psi}\otimes \ket{\psi}$.
|
||||
|
||||
Consider two pure states $\ket{\psi}$ and $\ket{\varphi}$, such that $U(\ket{\psi}\otimes \ket{s})=\ket{\psi}\otimes \ket{\psi}$ and $U(\ket{\varphi}\otimes \ket{s})=\ket{\varphi}\otimes \ket{\varphi}$. The inner product of the two equation yields:
|
||||
|
||||
$$
|
||||
\langle \psi|\varphi\rangle =(\langle \psi|\varphi\rangle)^2
|
||||
$$
|
||||
|
||||
This equation has only two solutions, either $\langle \psi|\varphi\rangle=0$ or $\langle \psi|\varphi\rangle=1$.
|
||||
|
||||
If $\langle \psi|\varphi\rangle=0$, then $\ket{\psi}=\ket{\varphi}$, no cloning for trivial case.
|
||||
|
||||
If $\langle \psi|\varphi\rangle=1$, then $\ket{\psi}$ and $\ket{\varphi}$ are orthogonal.
|
||||
|
||||
#### Proposition: Encoding 8 to 9 that correct 1 errors
|
||||
|
||||
Recover 1 qubit from a 9 qubit quantum system. (Shor code, 1995)
|
||||
|
||||
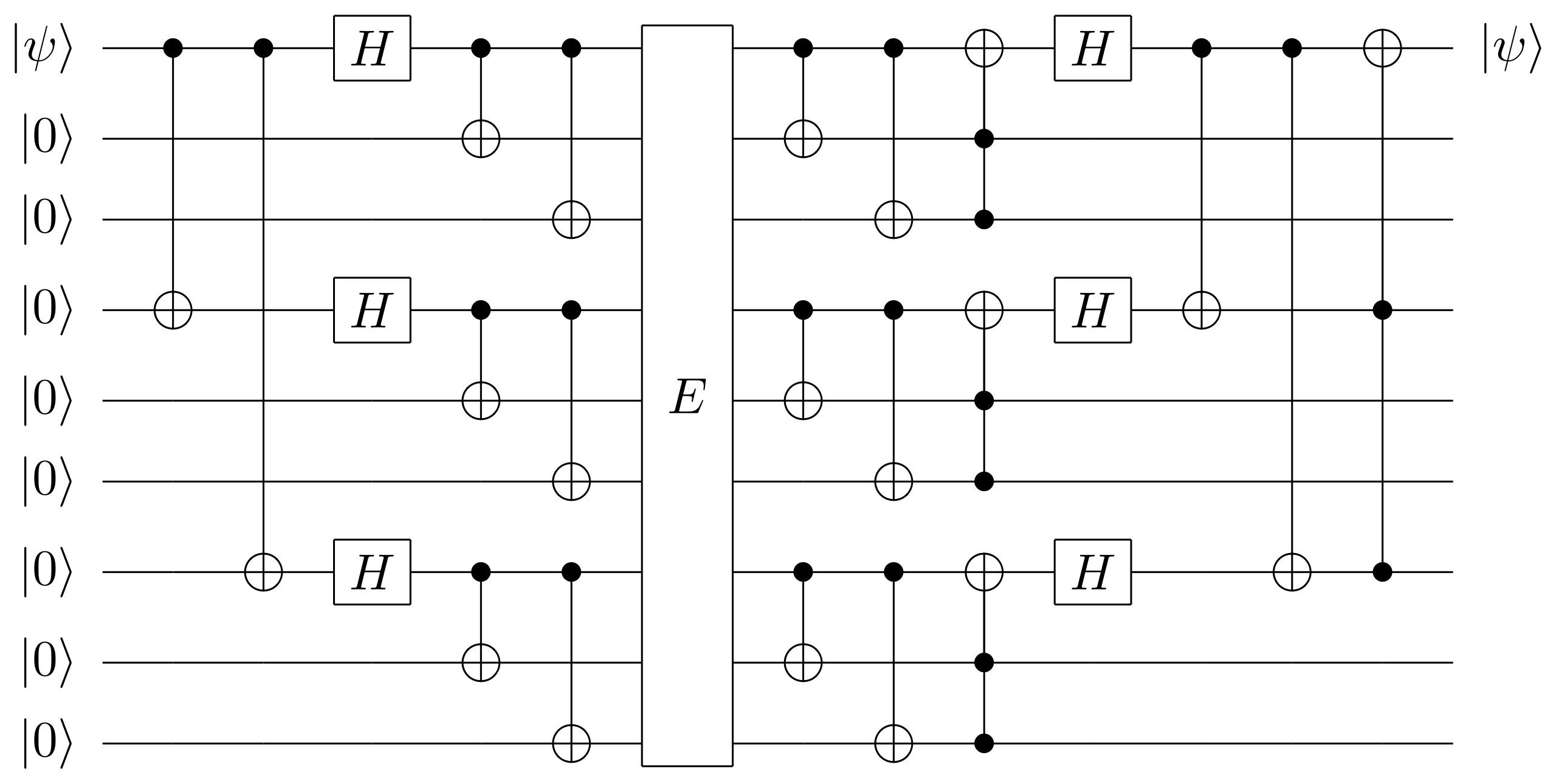
|
||||
|
||||
### Tools and related topics
|
||||
|
||||
#### Theoretical upper bound for quantum error-correcting code
|
||||
|
||||
From quantum information capacity of a quantum channel
|
||||
|
||||
$$
|
||||
\min\{1-H_2(2t/3n),H_2(\frac{1}{2}+\sqrt{(1-t/n)t/n})\}
|
||||
$$
|
||||
|
||||
#### Definition of quantum error-correcting code from binary linear error-correcting code
|
||||
|
||||
All the operations will be done in $\mathbb{F}_2=\{0,1\}$.
|
||||
|
||||
Consider two binary vectors $v=[v_1,...,v_n],v_i\in\{0,1\}$ and $w=[w_1,...,w_n],w_i\in\{0,1\}$ with size $n$.
|
||||
|
||||
Recall from our lecture that
|
||||
|
||||
$d$ denotes the Hamming weight of a vector.
|
||||
|
||||
$d_H(v,w)=\sum_{i=1}^{n}\begin{cases} 0 & \text{if } v_i=w_i \\ 1 & \text{if } v_i\neq w_i \end{cases}$ denotes the Hamming distance between $v$ and $w$.
|
||||
|
||||
$\operatorname{supp}(v)=\{i\in[n]:v_i\neq 0\}$ denotes the support of $v$.
|
||||
|
||||
$v|_S$ denotes the projection of $v$ onto the subspace $S$, we usually denote the $S$ by a set of coordinates, that is $S\subseteq[n]$.
|
||||
|
||||
When projecting a vector $v$ onto a another vector $w$, we usually write $v|_E\coloneqq v|_{\operatorname{supp} w}$.
|
||||
|
||||
When we have two vector we may use $v\leqslant w$ (Note that this is different than $\leq$ sign) to mean $\operatorname{supp}(v)\subseteq \operatorname{supp}(w)$.
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
Let $v=[1,0,0,1,1,1,1]$ and $w=[1,0,0,1,0,0,1]$, then $\operatorname{supp}(v)=\{1,4,5,6,7\}$, $\operatorname{supp}(w)=\{1,4,7\}$. Therefore $w\leqslant v$.
|
||||
|
||||
$v|_w=[v_1,v_4,v_7]=[1,1,0]$
|
||||
</details>
|
||||
|
||||
$\mathcal{C}$ denotes the code, a set of arbitrary binary vectors with length $n$.
|
||||
|
||||
$d(\mathcal{C})=\{d(v,w)|v,w\in\mathcal{C}\}$ denotes the minimum distance of the code.
|
||||
|
||||
If $\mathcal{C}$ is linear then the minimum distance is the minimum Hamming weight of a non-zero codeword.
|
||||
|
||||
A $[n,k,d]$ linear code is a linear code of $n$ bits codeword with $k$ message bits that can correct $d$ errors.
|
||||
|
||||
$R\coloneqq\frac{\operatorname{dim}\mathcal{C}}{n}$ is the rate of code $\mathcal{C}$.
|
||||
|
||||
$\mathcal{C}^{\perp}\coloneqq\{v\in\mathbb{F}_2^n:v\cdot w=0\text{ for all }w\in\mathcal{C}\}$ is the dual code of a code $\mathcal{C}$. From linear algebra, we know that $\dim\mathcal{C}^{\perp}+\dim\mathcal{C}=n$.
|
||||
|
||||
<details>
|
||||
<summary>Example used in the paper</summary>
|
||||
|
||||
Consider the $[7,4,3]$ Hamming code with generator matrix $G$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Proposition: Encoding $k$ to $n$ that correct $t$ errors
|
||||
|
||||
### Evaluation of paper
|
||||
|
||||
### Limitation and suggestions
|
||||
|
||||
### Further direction and research
|
||||
|
||||
#### Toric code, surface code
|
||||
|
||||
This is the topic I really want to dig into.
|
||||
|
||||
This method gives a [2nm+n+m+1, 1, min(n,m)] error correcting code with only needs local stabilizer checks and really interests me.
|
||||
|
||||
### References
|
||||
<iframe src="https://git.trance-0.com/Trance-0/CSE5313F1/raw/branch/main/latex/ZheyuanWu_CSE5313_FinalAssignment.pdf" width="100%" height="600px" style="border: none;" title="Embedded PDF Viewer">
|
||||
<!-- Fallback content for browsers that do not support iframes or PDFs within them -->
|
||||
<iframe src="https://git.trance-0.com/Trance-0/CSE5313F1/raw/branch/main/latex/ZheyuanWu_CSE5313_FinalAssignment.pdf" width="100%" height="500px">
|
||||
<p>Your browser does not support iframes. You can <a href="https://git.trance-0.com/Trance-0/CSE5313F1/raw/branch/main/latex/ZheyuanWu_CSE5313_FinalAssignment.pdf">download the PDF</a> file instead.</p>
|
||||
</iframe>
|
||||
|
||||
@@ -53,4 +53,4 @@ $$
|
||||
|
||||
This part is intentionally left blank and may be filled near the end of the semester, by assignments given in CSE5313.
|
||||
|
||||
[Link to self-contained report](../../CSE5313/Exam_reviews/CSE5313_F1.md)
|
||||
[Link to self-contained report](https://notenextra.trance-0.com/CSE5313/Exam_reviews/CSE5313_F1/)
|
||||
12
content/Math401/Math401_H1.md
Normal file
12
content/Math401/Math401_H1.md
Normal file
@@ -0,0 +1,12 @@
|
||||
# Honor Thesis
|
||||
|
||||
I made this little book for my Honor Thesis, showing the relevant parts of my work and background to understand my thesis.
|
||||
|
||||
Contents updated as displayed and based on my personal interest and progress with Prof.Feres.
|
||||
|
||||
|
||||
<iframe src="https://git.trance-0.com/Trance-0/HonorThesis/raw/branch/main/main.pdf" width="100%" height="600px" style="border: none;" title="Embedded PDF Viewer">
|
||||
<!-- Fallback content for browsers that do not support iframes or PDFs within them -->
|
||||
<iframe src="https://git.trance-0.com/Trance-0/HonorThesis/raw/branch/main/main.pdf" width="100%" height="500px">
|
||||
<p>Your browser does not support iframes. You can <a href="https://git.trance-0.com/Trance-0/HonorThesis/raw/branch/main/main.pdf">download the PDF</a> file instead.</p>
|
||||
</iframe>
|
||||
@@ -8,4 +8,5 @@ export default {
|
||||
Math401_N3: "Math 401, Notes 3",
|
||||
Freiwald_summer: "Math 401, Summer 2025: Freiwald research project notes",
|
||||
Extending_thesis: "Math 401, Fall 2025: Thesis notes",
|
||||
Math401_H1: "Math 401, Final Thesis"
|
||||
}
|
||||
@@ -21,7 +21,7 @@ If $\mathbb{R}_l$ is second countable, then for any real number $x$, there is an
|
||||
|
||||
Any such open sets is of the form $[x,x+\epsilon)\cap A$ with $\epsilon>0$ and any element of $A$ being larger than $\min(U_x)=x$.
|
||||
|
||||
In summary, for any $x\in \mathbb{R}$, there is an element $U_x\in \mathcal{B}$ with $(U_x)=x$. In particular, if $x\neq y$, then $U_x\neq U_y$. SO there is an injective map $f:\mathbb{R}\rightarrow \mathcal{B}$ sending $x$ to $U_x$. This implies that $\mathbb{B}$ is uncountable.
|
||||
In summary, for any $x\in \mathbb{R}$, there is an element $U_x\in \mathcal{B}$ with $(U_x)=x$. In particular, if $x\neq y$, then $U_x\neq U_y$. So there is an injective map $f:\mathbb{R}\rightarrow \mathcal{B}$ sending $x$ to $U_x$. This implies that $\mathcal{B}$ is uncountable.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
@@ -27,7 +27,7 @@ $$
|
||||
Let $(X,\mathcal{T})$ be a topological space. Let $\mathcal{C}\subseteq \mathcal{T}$ be a collection of subsets of $X$ satisfying the following property:
|
||||
|
||||
$$
|
||||
\forall U\in \mathcal{T}, \exists C\in \mathcal{C} \text{ such that } U\subseteq C
|
||||
\forall U\in \mathcal{T}, \exists C\in \mathcal{C} \text{ such that } C\subseteq U
|
||||
$$
|
||||
|
||||
Then $\mathcal{C}$ is a basis and the topology generated by $\mathcal{C}$ is $\mathcal{T}$.
|
||||
|
||||
100
content/Math4202/Math4202_L10.md
Normal file
100
content/Math4202/Math4202_L10.md
Normal file
@@ -0,0 +1,100 @@
|
||||
# Math4202 Topology II (Lecture 10)
|
||||
|
||||
## Algebraic Topology
|
||||
|
||||
### Path homotopy
|
||||
|
||||
|
||||
#### Theorem for properties of product of paths
|
||||
|
||||
1. If $f\simeq_p f_1, g\simeq_p g_1$, then $f*g\simeq_p f_1*g_1$. (Product is well-defined)
|
||||
2. $([f]*[g])*[h]=[f]*([g]*[h])$. (Associativity)
|
||||
3. Let $e_{x_0}$ be the constant path from $x_0$ to $x_0$, $e_{x_1}$ be the constant path from $x_1$ to $x_1$. Suppose $f$ is a path from $x_0$ to $x_1$.
|
||||
$$
|
||||
[e_{x_0}]*[f]=[f],\quad [f]*[e_{x_1}]=[f]
|
||||
$$
|
||||
(Right and left identity)
|
||||
4. Given $f$ in $X$ a path from $x_0$ to $x_1$, we define $\bar{f}$ to be the path from $x_1$ to $x_0$ where $\bar{f}(t)=f(1-t)$.
|
||||
$$
|
||||
f*\bar{f}=e_{x_0},\quad \bar{f}*f=e_{x_1}
|
||||
$$
|
||||
$$
|
||||
[f]*[\bar{f}]=[e_{x_0}],\quad [\bar{f}]*[f]=[e_{x_1}]
|
||||
$$
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
(1) If $f\simeq_p f_1$, $g\simeq_p g_1$, then $f*g\simeq_p f_1*g_1$.
|
||||
|
||||
Let $F$ be homotopy between $f$ and $f_1$, $G$ be homotopy between $g$ and $g_1$.
|
||||
|
||||
We can define
|
||||
|
||||
$$
|
||||
F*G:[0,1]\times [0,1]\to X,\quad F*G(s,t)=\left(F(-,t)*G(-,t)\right)(s)=\begin{cases}
|
||||
F(2s,t) & 0\leq s\leq \frac{1}{2}\\
|
||||
G(2s-1,t) & \frac{1}{2}\leq s\leq 1
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
$F*G$ is a homotopy between $f*g$ and $f_1*g_1$.
|
||||
|
||||
We can check this by enumerating the cases from definition of homotopy.
|
||||
|
||||
---
|
||||
|
||||
(2) $([f]*[g])*[h]=[f]*([g]*[h])$.
|
||||
|
||||
For $f*(g*h)$, along the interval $[0,\frac{1}{2}]$ we map $x_1\to x_2$, then along the interval $[\frac{1}{2},\frac{3}{4}]$ we map $x_2\to x_3$, then along the interval $[\frac{3}{4},1]$ we map $x_3\to x_4$.
|
||||
|
||||
For $(f*g)*h$, along the interval $[0,\frac{1}{4}]$ we map $x_1\to x_2$, then along the interval $[\frac{1}{4},\frac{1}{2}]$ we map $x_2\to x_3$, then along the interval $[\frac{1}{2},1]$ we map $x_3\to x_4$.
|
||||
|
||||
We can construct the homotopy between $f*(g*h)$ and $(f*g)*h$ as follows.
|
||||
|
||||
Let $f((4-2t)s)$ for $F(s,t)$,
|
||||
|
||||
when $t=0$, $F(s,0)=f(4s)\in f*(g*h)$, when $t=1$, $F(s,1)=f(2s)\in (f*g)*h$.
|
||||
|
||||
....
|
||||
|
||||
_We make the linear maps between $f*(g*h)$ and $(f*g)*h$ continuous, then $f*(g*h)\simeq_p (f*g)*h$. With our homotopy constructed above_
|
||||
|
||||
---
|
||||
|
||||
(3) $e_{x_0}*f\simeq_p f\simeq_p f*e_{x_1}$.
|
||||
|
||||
We can construct the homotopy between $e_{x_0}*f$ and $f$ as follows.
|
||||
|
||||
$$
|
||||
H(s,t)=\begin{cases}
|
||||
x_0 & t\geq 2s\\
|
||||
f(2s-t) & t\leq 2s
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
or you may induct from $f(\frac{s-t/2}{1-t/2})$ if you like.
|
||||
|
||||
---
|
||||
|
||||
(4) $f*\bar{f}=e_{x_0},\quad \bar{f}*f=e_{x_1}$.
|
||||
|
||||
Note that we don't need to reach $x_1$ every time.
|
||||
|
||||
$f_t=f(ts)$ $s\in[0,\frac{1}{2}]$.
|
||||
|
||||
$\bar{f}_t=\bar{f}(1-ts)$ $s\in[\frac{1}{2},1]$.
|
||||
|
||||
</details>
|
||||
|
||||
> [!CAUTION]
|
||||
>
|
||||
> Homeomorphism does not implies homotopy automatically.
|
||||
|
||||
#### Definition for the fundamental group
|
||||
|
||||
The fundamental group of $X$ at $x$ is defined to be
|
||||
|
||||
$$
|
||||
(\Pi_1(X,x),*)
|
||||
$$
|
||||
132
content/Math4202/Math4202_L11.md
Normal file
132
content/Math4202/Math4202_L11.md
Normal file
@@ -0,0 +1,132 @@
|
||||
# Math4201 Topology II (Lecture 11)
|
||||
|
||||
## Algebraic topology
|
||||
|
||||
### Fundamental group
|
||||
|
||||
The $*$ operation has the following properties:
|
||||
|
||||
#### Properties for the path product operation
|
||||
|
||||
Let $[f],[g]\in \Pi_1(X)$, for $[f]\in \Pi_1(X)$, let $s:\Pi_1(X)\to X, [f]\mapsto f(0)$ and $t:\Pi_1(X)\to X, [f]\mapsto f(1)$.
|
||||
|
||||
Note that $t([f])=s([g])$, $[f]*[g]=[f*g]\in \Pi_1(X)$.
|
||||
|
||||
This also satisfies the associativity. $([f]*[g])*[h]=[f]*([g]*[h])$.
|
||||
|
||||
We have left and right identity. $[f]*[e_{t(f)}]=[f], [e_{s(f)}]*[f]=[f]$.
|
||||
|
||||
We have inverse. $[f]*[\bar{x}]=[e_{s(f)}], [\bar{x}]*[f]=[e_{t(f)}]$
|
||||
|
||||
#### Definition for Groupoid
|
||||
|
||||
Let $f,g$ be paths where $g,f:[0,1]\to X$, and consider the function of all pathes in $G$, denoted as $\mathcal{G}$,
|
||||
|
||||
Set $t:\mathcal{G}\to X$ be the source map, for this case $t(f)=f(0)$, and $s:\mathcal{G}\to X$ be the target map, for this case $s(f)=f(1)$.
|
||||
|
||||
We define
|
||||
|
||||
$$
|
||||
\mathcal{G}^{(2)}=\{(f,g)\in \mathcal{G}\times \mathcal{G}|t(f)=s(g)\}
|
||||
$$
|
||||
|
||||
And we define the operation $*$ on $\mathcal{G}^{(2)}$ as the path product.
|
||||
|
||||
This satisfies the following properties:
|
||||
|
||||
- Associativity: $(f*g)*h=f*(g*h)$
|
||||
|
||||
Consider the function $\eta:X\to \mathcal{G}$, for this case $\eta(x)=e_{x}$.
|
||||
|
||||
- We have left and right identity: $\eta(t(f))*f=f, f*\eta(s(f))=f$
|
||||
|
||||
- Inverse: $\forall g\in \mathcal{G}, \exists g^{-1}\in \mathcal{G}, g*g^{-1}=\eta(s(g))$, $g^{-1}*g=\eta(t(g))$
|
||||
|
||||
#### Definition for loop
|
||||
|
||||
Let $x_0\in X$. A path starting and ending at $x_0$ is called a loop based at $x_0$.
|
||||
|
||||
#### Definition for the fundamental group
|
||||
|
||||
The fundamental group of $X$ at $x$ is defined to be
|
||||
|
||||
$$
|
||||
(\Pi_1(X,x),*)
|
||||
$$
|
||||
|
||||
where $*$ is the product operation, and $\Pi_1(X,x)$ is the set o homotopy classes of loops in $X$ based at $x$.
|
||||
|
||||
<details>
|
||||
<summary>Example of fundamental group</summary>
|
||||
|
||||
Consider $X=[0,1]$, with subspace topology from standard topology in $\mathbb{R}$.
|
||||
|
||||
$\Pi_1(X,0)=\{e\}$, (constant function at $0$) since we can build homotopy for all loops based at $0$ as follows $H(s,t)=(1-t)f(s)+t$.
|
||||
|
||||
And $\Pi_1(X,1)=\{e\}$, (constant function at $1$.)
|
||||
|
||||
---
|
||||
|
||||
Let $X=\{1,2\}$ with discrete topology.
|
||||
|
||||
$\Pi_1(X,1)=\{e\}$, (constant function at $1$.)
|
||||
|
||||
$\Pi_1(X,2)=\{e\}$, (constant function at $2$.)
|
||||
|
||||
---
|
||||
|
||||
Let $X=S^1$ be the circle.
|
||||
|
||||
$\Pi_1(X,1)=\mathbb{Z}$ (related to winding numbers, prove next week).
|
||||
|
||||
</details>
|
||||
|
||||
A natural question is, will the fundamental group depends on the basepoint $x$?
|
||||
|
||||
#### Definition for $\hat{\alpha}$
|
||||
|
||||
Let $\alpha$ be a path in $X$ from $x_0$ to $x_1$. $\alpha:[0,1]\to X$ such that $\alpha(0)=x_0$ and $\alpha(1)=x_1$. Define $\hat{\alpha}:\Pi_1(X,x_0)\to \Pi_1(X,x_1)$ as follows:
|
||||
|
||||
$$
|
||||
\hat{\alpha}(\beta)=[\bar{\alpha}]*[f]*[\alpha]
|
||||
$$
|
||||
|
||||
#### $\hat{\alpha}$ is a group homomorphism
|
||||
|
||||
$\hat{\alpha}$ is a group homomorphism between $(\Pi_1(X,x_0),*)$ and $(\Pi_1(X,x_1),*)$
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Let $f,g\in \Pi_1(X,x_0)$, then $\hat{\alpha}(f*g)=\hat{\alpha}(f)\hat{\alpha}(g)$
|
||||
|
||||
$$
|
||||
\begin{aligned}
|
||||
\hat{\alpha}(f*g)&=[\bar{\alpha}]*[f]*[g]*[\alpha]\\
|
||||
&=[\bar{\alpha}]*[f]*[e_{x_0}]*[g]*[\alpha]\\
|
||||
&=[\bar{\alpha}]*[f]*[\alpha]*[\bar{\alpha}]*[g]*[\alpha]\\
|
||||
&=([\bar{\alpha}]*[f]*[\alpha])*([\bar{\alpha}]*[g]*[\alpha])\\
|
||||
&=(\hat{\alpha}(f))*(\hat{\alpha}(g))
|
||||
\end{aligned}
|
||||
$$
|
||||
|
||||
---
|
||||
|
||||
Next, we will show that $\hat{\alpha}\circ \hat{\bar{\alpha}}([f])=[f]$, and $\hat{\bar{\alpha}}\circ \hat{\alpha}([f])=[f]$.
|
||||
|
||||
$$
|
||||
\begin{aligned}
|
||||
\hat{\alpha}\circ \hat{\bar{\alpha}}([f])&=\hat{\alpha}([\bar{\alpha}]*[f]*[\alpha])\\
|
||||
&=[\alpha]*[\bar{\alpha}]*[f]*[\alpha]*[\bar{\alpha}]\\
|
||||
&=[e_{x_0}]*[f]*[e_{x_1}]\\
|
||||
&=[f]
|
||||
\end{aligned}
|
||||
$$
|
||||
|
||||
The other case is the same
|
||||
|
||||
</details>
|
||||
|
||||
#### Corollary of fundamental group
|
||||
|
||||
If $X$ is path-connected and $x_0,x_1\in X$, then $\Pi_1(X,x_0)$ is isomorphic to $\Pi_1(X,x_1)$.
|
||||
119
content/Math4202/Math4202_L12.md
Normal file
119
content/Math4202/Math4202_L12.md
Normal file
@@ -0,0 +1,119 @@
|
||||
# Math4201 Topology II (Lecture 12)
|
||||
|
||||
## Algebraic topology
|
||||
|
||||
### Fundamental group
|
||||
|
||||
Recall from last lecture, the $(\Pi_1(X,x_0),*)$ is a group, and for any two points $x_0,x_1\in X$, the group $(\Pi_1(X,x_0),*)$ is isomorphic to $(\Pi_1(X,x_1),*)$ if $x_0,x_1$ is path connected.
|
||||
|
||||
> [!TIP]
|
||||
>
|
||||
> How does the $\hat{\alpha}$ (isomorphism between $(\Pi_1(X,x_0),*)$ and $(\Pi_1(X,x_1),*)$) depend on the choice of $\alpha$ (path) we choose?
|
||||
|
||||
#### Definition of simply connected
|
||||
|
||||
A space $X$ is simply connected if
|
||||
|
||||
- $X$ is [path-connected](https://notenextra.trance-0.com/Math4201/Math4201_L23/#definition-of-path-connected-space) ($\forall x_0,x_1\in X$, there exists a continuous function $\alpha:[0,1]\to X$ such that $\alpha(0)=x_0$ and $\alpha(1)=x_1$)
|
||||
- $\Pi_1(X,x_0)$ is the trivial group for some $x_0\in X$
|
||||
|
||||
<details>
|
||||
<summary>Example of simply connected space</summary>
|
||||
|
||||
Intervals are simply connected.
|
||||
|
||||
---
|
||||
|
||||
Any star-shaped is simply connected.
|
||||
|
||||
---
|
||||
|
||||
$S^1$ is not simply connected, but $n\geq 2$, then $S^n$ is simply connected.
|
||||
|
||||
</details>
|
||||
|
||||
#### Lemma for simply connected space
|
||||
|
||||
In a simply connected space $X$, and two paths having the same initial and final points are path homotopic.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Let $f,g$ be paths having the same initial and final points, then $f(0)=g(0)=x_0$ and $f(1)=g(1)=x_1$.
|
||||
|
||||
Therefore $[f]*[\bar{g}]\simeq_p [e_{x_0}]$ (by simply connected space assumption).
|
||||
|
||||
Then
|
||||
|
||||
$$
|
||||
\begin{aligned}
|
||||
[f]*[\bar{g}]&\simeq_p [e_{x_0}]\\
|
||||
([f]*[\bar{g}])*[g]&\simeq_p [e_{x_0}]*[g]\\
|
||||
[f]*([\bar{g}]*[g])&\simeq_p [e_{x_0}]*[g]\\
|
||||
[f]*[e_{x_1}]&\simeq_p [e_{x_0}]*[g]\\
|
||||
[f]&\simeq_p [g]
|
||||
\end{aligned}
|
||||
$$
|
||||
|
||||
</details>
|
||||
|
||||
#### Definition of group homomorphism induced by continuous map
|
||||
|
||||
Let $h:(X,x_0)\to (Y,y_0)$ be a continuous map, define $h_*:\Pi_1(X,x_0)\to \Pi_1(Y,y_0)$ where $h(x_0)=y_0$. by $h_*([f])=[h\circ f]$.
|
||||
|
||||
$h_*$ is called the group homomorphism induced by $h$ relative to $x_0$.
|
||||
|
||||
<details>
|
||||
<summary>Check the homomorphism property</summary>
|
||||
|
||||
$$
|
||||
\begin{aligned}
|
||||
h_*([f]*[g])&=h_*([f*g])\\
|
||||
&=[h_*[f*g]]\\
|
||||
&=[h_*[f]*h_*[g]]\\
|
||||
&=[h_*[f]]*[h_*[g]]\\
|
||||
&=h_*([f])*h_*([g])
|
||||
\end{aligned}
|
||||
$$
|
||||
|
||||
</details>
|
||||
|
||||
#### Theorem composite of group homomorphism
|
||||
|
||||
If $h:(X,x_0)\to (Y,y_0)$ and $k:(Y,y_0)\to (Z,z_0)$ are continuous maps, then $k_* \circ h_*:\Pi_1(X,x_0)\to \Pi_1(Z,z_0)$ where $h_*:\Pi_1(X,x_0)\to \Pi_1(Y,y_0)$, $k_*:\Pi_1(Y,y_0)\to \Pi_1(Z,z_0)$,is a group homomorphism.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Let $f$ be a loop based at $x_0$.
|
||||
|
||||
$$
|
||||
\begin{aligned}
|
||||
k_*(h_*([f]))&=k_*([h\circ f])\\
|
||||
&=[k\circ h\circ f]\\
|
||||
&=[(k\circ h)\circ f]\\
|
||||
&=(k\circ h)_*([f])\\
|
||||
\end{aligned}
|
||||
$$
|
||||
|
||||
</details>
|
||||
|
||||
#### Corollary of composite of group homomorphism
|
||||
|
||||
Let $\operatorname{id}:(X,x_0)\to (X,x_0)$ be the identity map. This induces $(\operatorname{id})_*:\Pi_1(X,x_0)\to \Pi_1(X,x_0)$.
|
||||
|
||||
If $h$ is a homeomorphism with the inverse $k$, with
|
||||
|
||||
$$
|
||||
k_*\circ h_*=(k\circ h)_*=(\operatorname{id})_*=I=(\operatorname{id})_*=(h\circ k)_*
|
||||
$$
|
||||
|
||||
This induced $h_*: \Pi_1(X,x_0)\to \Pi_1(Y,y_0)$ is an isomorphism.
|
||||
|
||||
#### Corollary for homotopy and group homomorphism
|
||||
|
||||
If $h,k:(X,x_0)\to (Y,y_0)$ are homotopic maps form $X$ to $Y$ such that the homotopy $H_t(x_0)=y_0,\forall t\in I$, then $h_*=k_*$.
|
||||
|
||||
$$
|
||||
h_*([f])=[h\circ f]\simeq_p[k\circ h]=k_*([f])
|
||||
$$
|
||||
59
content/Math4202/Math4202_L13.md
Normal file
59
content/Math4202/Math4202_L13.md
Normal file
@@ -0,0 +1,59 @@
|
||||
# Math4202 Topology II (Lecture 13)
|
||||
|
||||
## Algebraic Topology
|
||||
|
||||
### Covering space
|
||||
|
||||
#### Definition of partition into slice
|
||||
|
||||
Let $p:E\to B$ be a continuous surjective map. The open set $U\subseteq B$ is said to be evenly covered by $p$ if it's inverse image $p^{-1}(U)$ can be written as the union of **disjoint open sets** $V_\alpha$ in $E$. Such that for each $\alpha$, the restriction of $p$ to $V_\alpha$ is a homeomorphism of $V_\alpha$ onto $U$.
|
||||
|
||||
The collection of $\{V_\alpha\}$ is called a **partition** $p^{-1}(U)$ into slice.
|
||||
|
||||
_Stack of pancakes ($\{V_\alpha\}$) on plate $U$, each $V_\alpha$ is a pancake homeomorphic to $U$_
|
||||
|
||||
_Note that all the sets in the definition are open._
|
||||
|
||||
#### Definition of covering space
|
||||
|
||||
Let $p:E\to B$ be a continuous surjective map. If every point $b$ of $B$ has a neighborhood **evenly covered** by $p$, which means $p^{-1}(U)$ is partitioned into slice, then $p$ is called a covering map and $E$ is called a covering space.
|
||||
|
||||
<details>
|
||||
<summary>Examples of covering space</summary>
|
||||
|
||||
identity map is a covering map
|
||||
|
||||
---
|
||||
|
||||
Consider the $B\times \Gamma\to B$ with $\Gamma$ being the discrete topology with the projection map onto $B$.
|
||||
|
||||
This is a covering map.
|
||||
|
||||
---
|
||||
|
||||
Let $S^1=\{z\mid |z|=1\}$, then $p=z^n$ is a covering map to $S^1$.
|
||||
|
||||
Solving the inverse image for the $e^{i\theta}$ with $\epsilon$ interval, we can get $n$ slices for each neighborhood of $e^{i\theta}$, $-\epsilon< \theta< \epsilon$.
|
||||
|
||||
You can continue the computation and find the exact $\epsilon$ so that the inverse image of $p^{-1}$ is small and each interval don't intersect (so that we can make homeomorphism for each interval).
|
||||
|
||||
Usually, we don't choose the $U$ to be the whole space.
|
||||
|
||||
---
|
||||
|
||||
Consider the projection for the boundary of mobius strip into middle circle.
|
||||
|
||||
This is a covering map since the boundary of mobius strip is winding the middle circle twice, and for each point on the middle circle with small enough neighborhood, there will be two disjoint interval on the boundary of mobius strip that are homeomorphic to the middle circle.
|
||||
|
||||
</details>
|
||||
|
||||
#### Proposition of covering map is open map
|
||||
|
||||
If $p:E\to B$ is a covering map, then $p$ is an open map.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Consider arbitrary open set $V\subseteq E$, consider $U=p(V)$, for every point $q\in U$, with neighborhood $q\in W$, the inverse image of $W$ is open, continue next lecture.
|
||||
|
||||
</details>
|
||||
@@ -75,7 +75,8 @@ The map $f$ is continuous if and only if $g$ is continuous; $f$ is a quotient ma
|
||||
An $m$-dimensional **manifold** is a topological space $X$ that is
|
||||
|
||||
1. Hausdorff
|
||||
2. With a countable basis such that each point of $x$ of $X$ has a neighborhood that is homeomorphic to an open subset of $\mathbb{R}^m$.
|
||||
2. With a countable basis
|
||||
3. Each point of $x$ of $X$ has a neighborhood that is homeomorphic to an open subset of $\mathbb{R}^m$.
|
||||
|
||||
> [!NOTE]
|
||||
>
|
||||
|
||||
75
content/Math4202/Math4202_L4.md
Normal file
75
content/Math4202/Math4202_L4.md
Normal file
@@ -0,0 +1,75 @@
|
||||
# Math4202 Topology II (Lecture 4)
|
||||
|
||||
## Manifolds
|
||||
|
||||
### Imbedding of Manifolds
|
||||
|
||||
#### Definition of Manifold
|
||||
|
||||
An $m$-dimensional **manifold** is a topological space $X$ that is
|
||||
|
||||
1. Hausdorff
|
||||
2. With a countable basis
|
||||
3. Each point of $x$ of $X$ has a neighborhood that is homeomorphic to an open subset of $\mathbb{R}^m$. (local euclidean)
|
||||
|
||||
> [!NOTE]
|
||||
>
|
||||
> Try to find some example that satisfies some of the properties above but not a manifold.
|
||||
|
||||
1. Non-Hausdorff
|
||||
2. Non-countable basis
|
||||
- Consider $\mathbb{R}^\delta$ where the set is $\mathbb{R}$ with discrete topology. The basis must include all singleton sets in $\mathbb{R}$ therefore $\mathbb{R}^\delta$ is not second countable.
|
||||
3. Non-local euclidean
|
||||
- Consider the subspace topology over segment $[0,1]$ on real line, the subspace topology is not local euclidean since the open set containing the end point $[0,a)$ is not homeomorphic to open sets in $\mathbb{R}$. (if we remove the end point, in the segment space we have $(0,a)$ but in $\mathbb{R}$ is $(-a,0)\cup (0,a)$, which is not connected. Therefore cannot be homeomorphic to open sets in $\mathbb{R}$)
|
||||
- Any shape with intersection is not local euclidean.
|
||||
|
||||
#### Whitney's Embedding Theorem
|
||||
|
||||
If $X$ is a compact $m$-manifold, then $X$ can be imbedded in $\mathbb{R}^N$ for some positive integer $N$.
|
||||
|
||||
_In general, $X$ is not required to be compact. And $N$ is not too big. For non compact $X$, $N\leq 2m+1$ and for compact $X$, $N\leq 2m$._
|
||||
|
||||
#### Definition for partition of unity
|
||||
|
||||
Let $\{U_i\}_{i=1}^n$ be a finite open cover of topological space $X$. An indexed family of **continuous** function $\phi_i:X\to[0,1]$ for $i=1,...,n$ is said to be a **partition of unity** dominated by $\{U_i\}_{i=1}^n$ if
|
||||
|
||||
1. $\operatorname{supp}(\phi_i)=\overline{\{x\in X: \phi_i(x)\neq 0\}}\subseteq U_i$ (the closure of points where $\phi_i(x)\neq 0$ is in $U_i$) for all $i=1,...,n$
|
||||
2. $\sum_{i=1}^n \phi_i(x)=1$ for all $x\in X$ (partition of function to $1$)
|
||||
|
||||
#### Existence of finite partition of unity
|
||||
|
||||
Let $\{U_i\}_{i=1}^n$ be a finite open cover of a normal space $X$ (Every pair of closed sets in $X$ can be separated by two open sets in $X$).
|
||||
|
||||
Then there exists a partition of unity dominated by $\{U_i\}_{i=1}^n$.
|
||||
|
||||
_A more generalized version, If the space is paracompact, then there exists a partition of unity dominated by $\{U_i\}_{i\in I}$ with locally finite. (Theorem 41.7)_
|
||||
|
||||
<details>
|
||||
<summary>Proof for Whithney's Embedding Theorem</summary>
|
||||
|
||||
Since $X$ is a compact manifold, $\forall x\in X$, there is an open neighborhood $U_x$ of $x$ such that $U_x$ is homeomorphic to $\mathbb{R}^d$. That means there exists $\varphi_i:U_x\to \varphi(U_x)\subseteq \mathbb{R}^m$.
|
||||
|
||||
Where $\{U_x\}_{x\in X}$ is an open cover of $X$. Since $X$ is compact, there is a finite subcover $\bigcup_{i=1}^k U_{x_i}=X$.
|
||||
|
||||
Apply the existsence of partition of unity, we can find a partition of unity dominated by $\{U_{x_i}\}_{i=1}^k$. With family of functions $\phi_i:\mathbb{R}^d\to[0,1]$.
|
||||
|
||||
Define $h_i:X\to \mathbb{R}^m$ by
|
||||
|
||||
$$
|
||||
h_i(x)=\begin{cases}
|
||||
\phi_i(x)\varphi_i(x) & \text{if }x=x_i\\
|
||||
0 & \text{otherwise}
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
We claim that $h_i$ is continuous using pasting lemma.
|
||||
|
||||
On $U_i$, $h_i=\phi_i\varphi_i$ is product of two continuous functions therefore continuous.
|
||||
|
||||
On $X-\operatorname{supp}(\phi_i)$, $h_i=0$ is continuous.
|
||||
|
||||
By pasting lemma, $h_i$ is continuous.
|
||||
|
||||
Continue on next lecture.
|
||||
|
||||
</details>
|
||||
154
content/Math4202/Math4202_L5.md
Normal file
154
content/Math4202/Math4202_L5.md
Normal file
@@ -0,0 +1,154 @@
|
||||
# Math4202 Topology II (Lecture 5)
|
||||
|
||||
## Manifolds
|
||||
|
||||
### Imbedding of Manifolds
|
||||
|
||||
> [!NOTE]
|
||||
>
|
||||
> Suppose $f: X \to Y$ is an injective continuous map, where $X$ and $Y$ are topological spaces. Let $Z$ be the image set $f(X)$, considered as a subspace of $Y$, then the function $f’: X \to Z$ obtained by restricting the range of f is bijective. If f happens to be a homeomorphism of X with Z, we say that the map $f: X \to Y$ is a topological imbedding, or simply imbedding, of X in Y.
|
||||
|
||||
Recall from last lecture
|
||||
|
||||
#### Whitney's Embedding Theorem
|
||||
|
||||
If $X$ is a compact $m$-manifold, then $X$ can be imbedded in $\mathbb{R}^N$ for some positive integer $N$.
|
||||
|
||||
_In general, $X$ is not required to be compact. And $N$ is not too big. For non compact $X$, $N\leq 2m+1$ and for compact $X$, $N\leq 2m$._
|
||||
|
||||
#### Definition for partition of unity
|
||||
|
||||
Let $\{U_i\}_{i=1}^n$ be a finite open cover of topological space $X$. An indexed family of **continuous** function $\phi_i:X\to[0,1]$ for $i=1,...,n$ is said to be a **partition of unity** dominated by $\{U_i\}_{i=1}^n$ if
|
||||
|
||||
1. $\operatorname{supp}(\phi_i)=\overline{\{x\in X: \phi_i(x)\neq 0\}}\subseteq U_i$ (the closure of points where $\phi_i(x)\neq 0$ is in $U_i$) for all $i=1,...,n$
|
||||
2. $\sum_{i=1}^n \phi_i(x)=1$ for all $x\in X$ (partition of function to $1$)
|
||||
|
||||
#### Existence of finite partition of unity
|
||||
|
||||
Let $\{U_i\}_{i=1}^n$ be a finite open cover of a normal space $X$ (Every pair of closed sets in $X$ can be separated by two open sets in $X$).
|
||||
|
||||
Then there exists a partition of unity dominated by $\{U_i\}_{i=1}^n$.
|
||||
|
||||
_A more generalized version, If the space is paracompact, then there exists a partition of unity dominated by $\{U_i\}_{i\in I}$ with locally finite. (Theorem 41.7)_
|
||||
|
||||
<details>
|
||||
<summary>Proof for Whithney's Embedding Theorem</summary>
|
||||
|
||||
Since $X$ is a $m$ compact manifold, $\forall x\in X$, there is an open neighborhood $U_x$ of $x$ such that $U_x$ is homeomorphic to $\mathbb{R}^m$. That means there exists $\varphi_i:U_x\to \varphi(U_x)\subseteq \mathbb{R}^m$.
|
||||
|
||||
Where $\{U_x\}_{x\in X}$ is an open cover of $X$. Since $X$ is compact, there is a finite subcover $\bigcup_{i=1}^k U_{x_i}=X$.
|
||||
|
||||
Apply the [existence of partition of unity](#existence-of-finite-partition-of-unity), we can find a partition of unity dominated by $\{U_{x_i}\}_{i=1}^k$. With family of functions $\phi_i:\mathbb{R}^d\to[0,1]$.
|
||||
|
||||
Define $h_i:X\to \mathbb{R}^m$ by
|
||||
|
||||
$$
|
||||
h_i(x)=\begin{cases}
|
||||
\phi_i(x)\varphi_i(x) & \text{if }x=x_i\\
|
||||
0 & \text{otherwise}
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
We claim that $h_i$ is continuous using pasting lemma.
|
||||
|
||||
On $U_i$, $h_i=\phi_i\varphi_i$ is product of two continuous functions therefore continuous.
|
||||
|
||||
On $X-\operatorname{supp}(\phi_i)$, $h_i=0$ is continuous.
|
||||
|
||||
By pasting lemma, $h_i$ is continuous.
|
||||
|
||||
Define
|
||||
|
||||
$$
|
||||
F: X\to (\mathbb{R}^m\times \mathbb{R})^n
|
||||
$$
|
||||
|
||||
where $x\mapsto (h_1(x),\varphi_1(x),h_2(x),\varphi_2(x),\dots,h_n(x),\varphi_n(x))$
|
||||
|
||||
We want to show that $F$ is imbedding map.
|
||||
|
||||
**(a). $F$ is continuous**
|
||||
|
||||
since it is a product of continuous functions.
|
||||
|
||||
**(b). $F$ is injective**
|
||||
|
||||
that is, if $F(x_1)=F(x_2)$, then $x_1=x_2$.
|
||||
|
||||
By partition of unity, we have,
|
||||
|
||||
$h_1(x_1)=h_1(x_2), h_2(x_1)=h_2(x_2), \dots, h_n(x_1)=h_n(x_2)$.
|
||||
|
||||
And $\varphi_1(x_1)=\varphi_1(x_2), \varphi_2(x_1)=\varphi_2(x_2), \dots, \varphi_n(x_1)=\varphi_n(x_2)$.
|
||||
|
||||
Because $\sum_{i=1}^n \varphi_i(x_1)=1$, therefore the exists $\varphi_i(x_1)=\varphi_i(x_2)>0$.
|
||||
|
||||
Therefore $x1,x_2\in \operatorname{supp}(\phi_i)\subseteq U_i$.
|
||||
|
||||
By definition of $h$, $h_i(x_1)=h_i(x_2)$, $\varphi_i(x_1)\phi_i(x_1)=\varphi_i(x_2)\phi_i(x_2)$.
|
||||
|
||||
Using cancellation, $\phi_i(x_1)=\phi_i(x_2)$.
|
||||
|
||||
Therefore $x_1=x_2$ since $\phi_i(x_1)=\phi_i(x_2)$ is a homeomorphism.
|
||||
|
||||
_In this proof, $\varphi$ ensures the imbedding is properly defined on the open sets_
|
||||
|
||||
**(c). $F$ is a homeomorphism.**
|
||||
|
||||
Note that by [Theorem 26.6 on Munkres](https://notenextra.trance-0.com/Math4201/Math4201_L25/#theorem-of-closed-maps-from-compact-and-hausdorff-spaces), $F:X\to F(X)$ is a bijective map from a compact space to a Hausdorff space, therefore $F$ is a closed map.
|
||||
|
||||
Since $F$ is continuous, then $F^{-1}(C)$ where $C$ is a closed set in $F(X)$, $F^{-1}(C)$ is closed in $X$.
|
||||
|
||||
Therefore $F$ is a homeomorphism.
|
||||
|
||||
</details>
|
||||
|
||||
Then we will prove for the finite partition of unity.
|
||||
|
||||
<details>
|
||||
<summary>Proof for finite partition of unity</summary>
|
||||
|
||||
Some intuitions:
|
||||
|
||||
By definition for partition of unity, consider the sets $W_i,V_i$ defined as
|
||||
|
||||
$$
|
||||
W_i=f^{-1}_i((\frac{1}{2n},1])\subseteq f^{-1}_i([\frac{1}{2n},1])\subseteq V_i=f^{-1}_i((0,1])\subseteq \operatorname{supp}(f_i)\subseteq U_i
|
||||
$$
|
||||
|
||||
Note that $V_i$ is open and $\overline {V_i}\subseteq U_i$.
|
||||
|
||||
And $\bigcup_{i=1}^n V_i=X$.
|
||||
|
||||
and $W_i$ is open and $\overline{W_i}\subseteq V_i$.
|
||||
|
||||
And $\bigcup_{i=1}^n W_i=X$.
|
||||
|
||||
---
|
||||
|
||||
Step 1: $\exists$ V_i$ ope subsets $i=1,\dots,n$ such that $\overline{V_i}\subseteq U_i$, and $\bigcup_{i=1}^n V_i=X$.
|
||||
|
||||
For $i=1$, consider $A_1=X-(U_2\cup U_3\cup \dots \cup U_n)$. Therefore $A_1$ is closed, and $A_1\cup U_1=X$.
|
||||
|
||||
So $A_1\subseteq U_1$.
|
||||
|
||||
Note that $A_1$ and $X-U_1$ are disjoint closed subsets of $X$.
|
||||
|
||||
Since $X$ is normal, we can separate disjoint closed subsets $A_1$ and $X-U_1$.
|
||||
|
||||
So we have $A_1\subset V_1\subseteq \overline{V_1}\subseteq U_1$.
|
||||
|
||||
For $i=2$, note that $V_1\cup\left( \bigcup_{i=2}^n U_i\right)=X$,
|
||||
|
||||
Take $A_2=X-\left(V_1\cup\left( \bigcup_{i=3}^n U_i\right)\right)$ (skipping $U_2$).
|
||||
|
||||
Then we have $V_2\subseteq \overline{V_2}\subseteq U_2$.
|
||||
|
||||
For $i=j$, we have
|
||||
|
||||
$$
|
||||
A_j=X-\left(\left(\bigcup_{i=1}^{j-1}V_i\right)\cup \left(\bigcup_{i=j+1}^n U_i\right)\right)
|
||||
$$
|
||||
|
||||
Continue next lecture.
|
||||
</details>
|
||||
164
content/Math4202/Math4202_L6.md
Normal file
164
content/Math4202/Math4202_L6.md
Normal file
@@ -0,0 +1,164 @@
|
||||
# Math4202 Topology II (Lecture 6)
|
||||
|
||||
## Manifolds
|
||||
|
||||
### Imbedding of Manifolds
|
||||
|
||||
#### Definition for partition of unity
|
||||
|
||||
Let $\{U_i\}_{i=1}^n$ be a finite open cover of topological space $X$. An indexed family of **continuous** function $\phi_i:X\to[0,1]$ for $i=1,...,n$ is said to be a **partition of unity** dominated by $\{U_i\}_{i=1}^n$ if
|
||||
|
||||
1. $\operatorname{supp}(\phi_i)=\overline{\{x\in X: \phi_i(x)\neq 0\}}\subseteq U_i$ (the closure of points where $\phi_i(x)\neq 0$ is in $U_i$) for all $i=1,...,n$
|
||||
2. $\sum_{i=1}^n \phi_i(x)=1$ for all $x\in X$ (partition of function to $1$)
|
||||
|
||||
#### Existence of finite partition of unity
|
||||
|
||||
Let $\{U_i\}_{i=1}^n$ be a **finite open cover** of a **normal** space $X$ (Every pair of closed sets in $X$ can be separated by two open sets in $X$).
|
||||
|
||||
Then there exists a partition of unity dominated by $\{U_i\}_{i=1}^n$.
|
||||
|
||||
_A more generalized version, If the space is paracompact, then there exists a partition of unity dominated by $\{U_i\}_{i\in I}$ with locally finite. (Theorem 41.7)_
|
||||
|
||||
We will prove for the finite partition of unity.
|
||||
|
||||
<details>
|
||||
<summary>Proof for finite partition of unity</summary>
|
||||
|
||||
Some intuitions:
|
||||
|
||||
By definition for partition of unity, consider the sets $W_i,V_i$ defined as
|
||||
|
||||
$$
|
||||
W_i=f^{-1}_i((\frac{1}{2n},1])\subseteq f^{-1}_i([\frac{1}{2n},1])\subseteq V_i=f^{-1}_i((0,1])\subseteq \operatorname{supp}(f_i)\subseteq U_i
|
||||
$$
|
||||
|
||||
$$
|
||||
V_1\subseteq \overline{V_1}\subseteq U_1
|
||||
$$
|
||||
|
||||
Note that $V_i$ is open and $\overline {V_i}\subseteq U_i$.
|
||||
|
||||
And $\bigcup_{i=1}^n V_i=X$.
|
||||
|
||||
and $W_i$ is open and $\overline{W_i}\subseteq V_i$.
|
||||
|
||||
And $\bigcup_{i=1}^n W_i=X$.
|
||||
|
||||
---
|
||||
|
||||
**Step 1**:
|
||||
|
||||
$\exists$ V_i$ ope subsets $i=1,\dots,n$ such that $\overline{V_i}\subseteq U_i$, and $\bigcup_{i=1}^n V_i=X$.
|
||||
|
||||
For $i=1$, consider $A_1=X-(U_2\cup U_3\cup \dots \cup U_n)$. Therefore $A_1$ is closed, and $A_1\cup U_1=X$.
|
||||
|
||||
So $A_1\subseteq U_1$.
|
||||
|
||||
Note that $A_1$ and $X-U_1$ are disjoint closed subsets of $X$.
|
||||
|
||||
Since $X$ is normal, we can separate disjoint closed subsets $A_1$ and $X-U_1$.
|
||||
|
||||
So we have $A_1\subset V_1\subseteq \overline{V_1}\subseteq U_1$ (by [normal space proposition](https://notenextra.trance-0.com/Math4201/Math4201_L37/#proposition-of-normal-spaces)).
|
||||
|
||||
For $i=2$, note that $V_1\cup\left( \bigcup_{i=2}^n U_i\right)=X$,
|
||||
|
||||
Take $A_2=X-\left(V_1\cup\left( \bigcup_{i=3}^n U_i\right)\right)$ (skipping $U_2$).
|
||||
|
||||
Then we have $V_2\subseteq \overline{V_2}\subseteq U_2$.
|
||||
|
||||
For $i=j$, we have
|
||||
|
||||
$$
|
||||
A_j=X-\left(\left(\bigcup_{i=1}^{j-1}V_i\right)\cup \left(\bigcup_{i=j+1}^n U_i\right)\right)
|
||||
$$
|
||||
|
||||
and $\bigcup_{i=1}^n V_i=X$.
|
||||
|
||||
Repeat the above construction for $\{V_i\}_{i=1}^n$.
|
||||
|
||||
Then we have $\{W_i\}_{i=1}^n$ open and $W_i\subseteq \overline{W_i}\subseteq V_i\subseteq \overline{V_i}\subseteq U_i$.
|
||||
|
||||
And $\bigcup_{i=1}^n W_i=X$.
|
||||
|
||||
**Step 2**:
|
||||
|
||||
Using [Urysohn's lemma](https://notenextra.trance-0.com/Math4201/Math4201_L37/#urysohn-lemma). To construct the partition of unity $\phi_i$.
|
||||
|
||||
> [!NOTE]
|
||||
>
|
||||
> Suppose
|
||||
>
|
||||
> - $X$ be a normal space
|
||||
> - $Z_1,Z_2\subseteq X$ are closed
|
||||
> - $Z_1$ and $Z_2$ are disjoint
|
||||
>
|
||||
> Then:
|
||||
>
|
||||
> There exists $f:X\to[0,1]$ such that
|
||||
>
|
||||
> - $f(Z_1)=\{0\}$ and $f(Z_2)=\{1\}$
|
||||
> - $f$ is continuous.
|
||||
|
||||
Since $W_1\subseteq \overline{W_1}\subseteq V_1\subseteq \overline{V_1}\subseteq U_1$,
|
||||
|
||||
Note that $\overline{W_1}$ and $X-V_1$ are two disjoint closed subsets of normal space $X$
|
||||
|
||||
Then we can have $f_1:X\to[0,1]$ such that $f_1(\overline{W_1})=\{0\}$ and $f_1(X-V_1)=\{1\}$.
|
||||
|
||||
Then we have the remaining list of function $f_2,\dots,f_n$.
|
||||
|
||||
Recall the definition for support of functions $\operatorname{supp}(f_i)=\overline{\{x\in X: f_i(x)>0\}}$. Since $f_i(x)=0$ for $x\in X-V_i$, we have $\operatorname{supp}(f_i)\subseteq \overline{V_i}$
|
||||
|
||||
Next we need to check $\sum_{i=1}^n f_i(x)=1$ for all $x\in X$.
|
||||
|
||||
Note that $\forall x\in X$, since $\bigcup_{i=1}^n W_i=X$, then there exists $i$ such that $x\in W_i$, thus $f_i(x)=1$.
|
||||
|
||||
And $\sum _{i=1}^n f_i(x)\geq 1$.
|
||||
|
||||
Then we do normalization for our value. Set $F(x)=\sum_{i=1}^n f_i(x)$.
|
||||
|
||||
Since $F(x)$ is sum of continuous functions, $F$ is continuous.
|
||||
|
||||
Then we define $\phi_i=f_i/F(x)$, since $F(x)\geq 1$, we are safe to divide by $F(x)$ and $\phi_i(x)$ is continuous.
|
||||
|
||||
And $\operatorname{supp}(\phi_i)=\operatorname{supp}(f_i)\subseteq \overline{V_i}\subseteq U_i$.
|
||||
|
||||
And $\sum_{i=1}^n \phi_i(x)=\frac{\sum_{i=1}^n f_i(x)}{F(x)}=\frac{F(x)}{F(x)}=1$ for all $x\in X$.
|
||||
|
||||
</details>
|
||||
|
||||
### Some Extension
|
||||
|
||||
#### Definition of paracompact space
|
||||
|
||||
Locally finite: $\forall x\in X$, $\exists$ open $x\in U$ such that $U$ only intersects finitely many open sets in $\mathcal{B}$.
|
||||
|
||||
A space $X$ is paracompact if every open cover $A$ of $X$ has a **locally finite** refinement $\mathcal{B}$ of $A$ that covers $X$.
|
||||
|
||||
## Algebraic Topology
|
||||
|
||||
Homeomorphism: A topological space $X$ is homeomorphic to a topological space $Y$ if there exists a homeomorphism $f:X\to Y$
|
||||
|
||||
- $f$ is continuous
|
||||
- $f^{-1}$ is continuous
|
||||
- $f$ is bijective
|
||||
|
||||
Equivalence relation: If $\sim$ satisfies the following:
|
||||
|
||||
- $\sim$ is reflexive $\forall x\in X, x\sim x$
|
||||
- $\sim$ is symmetric $\forall x,y\in X, x\sim y\implies y\sim x$
|
||||
- $\sim$ is transitive $\forall x,y,z\in X, x\sim y, y\sim z\implies x\sim z$
|
||||
|
||||
Homeomorphism is an equivalence relation.
|
||||
|
||||
- Reflexive: identity map
|
||||
- Symmetric: inverse map is also homeomorphism
|
||||
- Transitive: composition of homeomorphism is also homeomorphism
|
||||
|
||||
Main Question: classify topological space up to homeomorphism.
|
||||
|
||||
### Invariant in Mathematics
|
||||
|
||||
Quantities associated with topological spaces that don't change under homeomorphism.
|
||||
|
||||
We want to use some algebraic tools to classify topological spaces.
|
||||
63
content/Math4202/Math4202_L7.md
Normal file
63
content/Math4202/Math4202_L7.md
Normal file
@@ -0,0 +1,63 @@
|
||||
# Math4202 Topology II (Lecture 7)
|
||||
|
||||
## Algebraic Topology
|
||||
|
||||
Classify 2-dimensional topological manifolds (connected) up to homeomorphism/homotopy equivalence.
|
||||
|
||||
Use fundamental groups.
|
||||
|
||||
We want to show that:
|
||||
|
||||
1. The fundamental group is invariant under the equivalence relation.
|
||||
2. develop some methods to compute the groups.
|
||||
3. 2-dimensional topological spaces with the same fundamental group are equivalent (homeomorphism).
|
||||
|
||||
### Homotopy of paths
|
||||
|
||||
#### Definition of path
|
||||
|
||||
If $f$ and $f'$ are two continuous maps from $X$ to $Y$, where $X$ and $Y$ are topological spaces. Then we say that $f$ is homotopic to $f'$ if there exists a continuous map $F:X\times [0,1]\to Y$ such that $F(x,0)=f(x)$ and $F(x,1)=f'(x)$ for all $x\in X$.
|
||||
|
||||
The map $F$ is called a homotopy between $f$ and $f'$.
|
||||
|
||||
We use $f\simeq f'$ to mean that $f$ is homotopic to $f'$.
|
||||
|
||||
#### Definition of homotopic equivalence map
|
||||
|
||||
Let $f:X\to Y$ and $g:Y\to X$ be two continuous maps. If $f\circ g:Y\to Y$ and $g\circ f:X\to X$ are homotopic to the identity maps $\operatorname{id}_Y$ and $\operatorname{id}_X$, then $f$ and $g$ are homotopic equivalence maps. And the two spaces $X$ and $Y$ are homotopy equivalent.
|
||||
|
||||
> [!NOTE]
|
||||
>
|
||||
> This condition is weaker than homeomorphism. (In homeomorphism, let $g=f^{-1}$, we require $g\circ f=\operatorname{id}_X$ and $f\circ g=\operatorname{id}_Y$.)
|
||||
|
||||
<details>
|
||||
<summary>Example of homotopy equivalence maps</summary>
|
||||
|
||||
Let $X=\{a\}$ and $Y=[0,1]$ with standard topology.
|
||||
|
||||
Consider $f:X\to Y$ by $f(a)=0$ and $g:Y\to X$ by $g(y)=a$, where $y\in [0,1]$.
|
||||
|
||||
$g\circ f=\operatorname{id}_X$ and $f\circ g=[0,1]\mapsto 0$.
|
||||
|
||||
$g\circ f\simeq \operatorname{id}_X$
|
||||
|
||||
and $f\circ g\simeq \operatorname{id}_Y$.
|
||||
|
||||
Consider $F:X\times [0,1]\to Y$ by $F(a,0)=0$ and $F(a,t)=(1-t)y$. $F$ is continuous and homotopy between $f\circ g$ and $\operatorname{id}_Y$.
|
||||
|
||||
This gives example of homotopy but not homeomorphism.
|
||||
|
||||
</details>
|
||||
|
||||
#### Definition of null homology
|
||||
|
||||
If $f:X\to Y$ is homotopy to a constant map. $f$ is called null homotopy.
|
||||
|
||||
#### Definition of path homotopy
|
||||
|
||||
Let $f,f':I\to X$ be a continuous maps from an interval $I=[0,1]$ to a topological space $X$.
|
||||
|
||||
Two pathes $f$ and $f'$ are path homotopic if
|
||||
|
||||
- there exists a continuous map $F:I\times [0,1]\to X$ such that $F(i,0)=f(i)$ and $F(i,1)=f'(i)$ for all $i\in I$.
|
||||
- $F(s,0)=f(0)$ and $F(s,1)=f(1)$, $\forall s\in I$.
|
||||
88
content/Math4202/Math4202_L8.md
Normal file
88
content/Math4202/Math4202_L8.md
Normal file
@@ -0,0 +1,88 @@
|
||||
# Math4202 Topology II (Lecture 8)
|
||||
|
||||
## Algebraic Topology
|
||||
|
||||
### Path homotopy
|
||||
|
||||
#### Recall definition of path homotopy
|
||||
|
||||
Let $f,f':I\to X$ be a continuous maps from an interval $I=[0,1]$ to a topological space $X$.
|
||||
|
||||
Two pathes $f$ and $f'$ are path homotopic if
|
||||
|
||||
- there exists a continuous map $F:I\times [0,1]\to X$ such that $F(i,0)=f(i)$ and $F(i,1)=f'(i)$ for all $i\in I$.
|
||||
- $F(s,0)=f(0)$ and $F(s,1)=f(1)$, $\forall s\in I$.$F(s,0)=f(0)$ and $F(s,1)=f(1)$, $\forall s\in I$
|
||||
|
||||
#### Lemma: Homotopy defines an equivalence relation
|
||||
|
||||
The $\simeq$, $\simeq_p$ are both equivalence relations.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
**Reflexive**:
|
||||
|
||||
$f:I\to X$, $F:I\times I\to X$, $F(s,t)=f(s)$.
|
||||
|
||||
$F$ is a homotopy between $f$ and $f$ itself.
|
||||
|
||||
**Symmetric**:
|
||||
|
||||
Suppose $f,g:I\to X$,
|
||||
|
||||
$F:I\times I\to X$ is a homotopy between $f$ and $g$.
|
||||
|
||||
Let $H: I\times I\to X$ be a homotopy between $g$ and $f$ defined as follows:
|
||||
|
||||
$H(s,t)=F(s,1-t)$.
|
||||
|
||||
$H(s,0)=F(s,1)=g(s)$, $H(s,1)=F(s,0)=f(s)$.
|
||||
|
||||
Therefore $H$ is a homotopy between $g$ and $f$.
|
||||
|
||||
**Transitive**:
|
||||
|
||||
Suppose we have $f\simeq_p g$ with homotopy $F_1$, and $g\simeq_p h$ with homotopy $F_2$.
|
||||
|
||||
Then we can glue the two homotopies together to get a homotopy $F$ between $f$ and $h$ using pasting lemma.
|
||||
|
||||
$F(s,t)=(F_1*F_2)(s,t)\coloneqq\begin{cases}
|
||||
F_1(s,2t), & t\in [0,\frac{1}{2}]\\
|
||||
F_2(s,2t-1), & t\in [\frac{1}{2},1]
|
||||
\end{cases}$
|
||||
|
||||
Therefore $f\simeq_p h$ with homotopy $F$.
|
||||
|
||||
</details>
|
||||
|
||||
> [!NOTE]
|
||||
>
|
||||
> We use $[x]$ to denote the equivalence class of $x$.
|
||||
|
||||
<details>
|
||||
<summary>Example of equivalence classes in path homotopy</summary>
|
||||
|
||||
Let $X=\{pt\}$, $\operatorname{Path}(X)=\{\text{constant map}\}$.$\operatorname{Path}/_{\simeq_p}(X)=\{[\text{constant map}]\}$.
|
||||
|
||||
---
|
||||
|
||||
$X=\{p,q\}$ with discrete topology, $\operatorname{Path}(X)=\{f_{p},f_{q}\}$.$\operatorname{Path}/_{\simeq_p}(X)=\{[f_{p}], [f_{q}]\}$
|
||||
|
||||
This applied to all discrete topological spaces.
|
||||
|
||||
---
|
||||
|
||||
Let $X=\mathbb{R}$ with standard topology.
|
||||
|
||||
$\operatorname{Path}(X)=\{f:[0,1]\to \mathbb{R}\in C^0\}$
|
||||
|
||||
Let $f_1,f_2:[0,1]\to \mathbb{R}$ where $f_1(0)=f_2(0)$, $f_1(1)=f_2(1)$.
|
||||
|
||||
Then we can construct a homotopy between $f_1$ and $f_2$.
|
||||
|
||||
$F:[0,1]\times [0,1]\to \mathbb{R}$, $F(s,t)=(1-t)f_1(s)+tf_2(s)$ is a homotopy between $f_1$ and $f_2$.
|
||||
|
||||
$\operatorname{Path}/_{\simeq_p}(X)=\{(x_1,x_1)|x_1,x_2\in \mathbb{R}\}$
|
||||
|
||||
This applies to any convex space $V$ in $\mathbb{R}^n$.
|
||||
</details>
|
||||
145
content/Math4202/Math4202_L9.md
Normal file
145
content/Math4202/Math4202_L9.md
Normal file
@@ -0,0 +1,145 @@
|
||||
# Math4202 Topology II (Lecture 9)
|
||||
|
||||
## Algebraic Topology
|
||||
|
||||
### Path homotopy
|
||||
|
||||
Consider the space of paths up to homotopy equivalence.
|
||||
|
||||
$$
|
||||
\operatorname{Path}/\simeq_p(X) =\Pi_1(X)
|
||||
$$
|
||||
|
||||
We want to impose some group structure on $\operatorname{Path}/\simeq_p(X)$.
|
||||
|
||||
Consider the $*$ operation on $\operatorname{Path}/\simeq_p(X)$.
|
||||
|
||||
Let $f,g:[0,1]\to X$ be two paths, where $f(0)=a$, $f(1)=g(0)=b$ and $g(1)=c$.
|
||||
|
||||
$$
|
||||
f*g:[0,1]\to X,\quad f*g(t)=\begin{cases}
|
||||
f(2t) & 0\leq t\leq \frac{1}{2}\\
|
||||
g(2t-1) & \frac{1}{2}\leq t\leq 1
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
This connects our two paths.
|
||||
|
||||
#### Definition for product of paths
|
||||
|
||||
Given $f$ a path in $X$ from $x_0$ to $x_1$ and $g$ a path in $X$ from $x_1$ to $x_2$.
|
||||
|
||||
Define the product $f*g$ of $f$ and $g$ to be the map $h:[0,1]\to X$.
|
||||
|
||||
#### Definition for equivalent classes of paths
|
||||
|
||||
$\Pi_1(X,x)$ is the equivalent classes of paths starting and ending at $x$.
|
||||
|
||||
On $\Pi_1(X,x)$,, we define $\forall [f],[g],[f]*[g]=[f*g]$.
|
||||
|
||||
$$
|
||||
[f]\coloneqq \{f_i:[0,1]\to X|f_0(0)=f(0),f_i(1)=f(1)\}
|
||||
$$
|
||||
|
||||
#### Lemma
|
||||
|
||||
If we have some path $k:X\to Y$ is a continuous map, and if $F$ is path homotopy between $f$ and $f'$ in $X$, then $k\circ F$ is path homotopy between $k\circ f$ and $k\circ f'$ in $Y$.
|
||||
|
||||
If $k:X\to Y$ is a continuous map, and $f,g$ are two paths in $X$ with $f(1)=g(0)$, then
|
||||
|
||||
$$
|
||||
(k\circ f)*(k\circ g)=k\circ(f*g)
|
||||
$$
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
We check the definition of path homotopy.
|
||||
|
||||
$k\circ F:I\times I\to Y$ is continuous.
|
||||
|
||||
$k\circ F(s,0)=k(F(s,0))=k(f(s))=k\circ f(s)$.
|
||||
|
||||
$k\circ F(s,1)=k(F(s,1))=k(f'(s))=k\circ f'(s)$.
|
||||
|
||||
$k\circ F(0,t)=k(F(0,t))=k(f(0))=k(x_0$.
|
||||
|
||||
$k\circ F(1,t)=k(F(1,t))=k(f'(1))=k(x_1)$.
|
||||
|
||||
Therefore $k\circ F$ is path homotopy between $k\circ f$ and $k\circ f'$ in $Y$.
|
||||
|
||||
---
|
||||
|
||||
For the second part of the lemma, we proceed from the definition.
|
||||
|
||||
$$
|
||||
(k\circ f)*(k\circ g)(t)=\begin{cases}
|
||||
k\circ f(2t) & 0\leq t\leq \frac{1}{2}\\
|
||||
k\circ g(2t-1) & \frac{1}{2}\leq t\leq 1
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
and
|
||||
|
||||
$$
|
||||
k\circ(f*g)=k(f*g(t))=k\left(\begin{cases}
|
||||
f(2t) & 0\leq t\leq \frac{1}{2}\\
|
||||
g(2t-1) & \frac{1}{2}\leq t\leq 1
|
||||
\end{cases}\right)=\begin{cases}
|
||||
k(f(2t))=k\circ f(2t) & 0\leq t\leq \frac{1}{2}\\
|
||||
k(g(2t-1))=k\circ g(2t-1) & \frac{1}{2}\leq t\leq 1
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
</details>
|
||||
|
||||
#### Theorem for properties of product of paths
|
||||
|
||||
1. If $f\simeq_p f_1, g\simeq_p g_1$, then $f*g\simeq_p f_1*g_1$. (Product is well-defined)
|
||||
2. $([f]*[g])*[h]=[f]*([g]*[h])$. (Associativity)
|
||||
3. Let $e_{x_0}$ be the constant path from $x_0$ to $x_0$, $e_{x_1}$ be the constant path from $x_1$ to $x_1$. Suppose $f$ is a path from $x_0$ to $x_1$.
|
||||
$$
|
||||
[e_{x_0}]*[f]=[f],\quad [f]*[e_{x_1}]=[f]
|
||||
$$
|
||||
(Right and left identity)
|
||||
4. Given $f$ in $X$ a path from $x_0$ to $x_1$, we define $\bar{f}$ to be the path from $x_1$ to $x_0$ where $\bar{f}(t)=f(1-t)$.
|
||||
$$
|
||||
f*\bar{f}=e_{x_0},\quad \bar{f}*f=e_{x_1}
|
||||
$$
|
||||
$$
|
||||
[f]*[\bar{f}]=[e_{x_0}],\quad [\bar{f}]*[f]=[e_{x_1}]
|
||||
$$
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
(1) If $f\simeq_p f_1$, $g\simeq_p g_1$, then $f*g\simeq_p f_1*g_1$.
|
||||
|
||||
Let $F$ be homotopy between $f$ and $f_1$, $G$ be homotopy between $g$ and $g_1$.
|
||||
|
||||
We can define
|
||||
|
||||
$$
|
||||
F*G:[0,1]\times [0,1]\to X,\quad F*G(s,t)=\left(F(-,t)*G(-,t)\right)(s)=\begin{cases}
|
||||
F(2s,t) & 0\leq s\leq \frac{1}{2}\\
|
||||
G(2s-1,t) & \frac{1}{2}\leq s\leq 1
|
||||
\end{cases}
|
||||
$$
|
||||
|
||||
$F*G$ is a homotopy between $f*g$ and $f_1*g_1$.
|
||||
|
||||
We can check this by enumerating the cases from definition of homotopy.
|
||||
|
||||
---
|
||||
|
||||
Continue next time.
|
||||
|
||||
</details>
|
||||
|
||||
#### Definition for the fundamental group
|
||||
|
||||
The fundamental group of $X$ at $x$ is defined to be
|
||||
|
||||
$$
|
||||
(\Pi_1(X,x),*)
|
||||
$$
|
||||
@@ -6,4 +6,14 @@ export default {
|
||||
Math4202_L1: "Topology II (Lecture 1)",
|
||||
Math4202_L2: "Topology II (Lecture 2)",
|
||||
Math4202_L3: "Topology II (Lecture 3)",
|
||||
Math4202_L4: "Topology II (Lecture 4)",
|
||||
Math4202_L5: "Topology II (Lecture 5)",
|
||||
Math4202_L6: "Topology II (Lecture 6)",
|
||||
Math4202_L7: "Topology II (Lecture 7)",
|
||||
Math4202_L8: "Topology II (Lecture 8)",
|
||||
Math4202_L9: "Topology II (Lecture 9)",
|
||||
Math4202_L10: "Topology II (Lecture 10)",
|
||||
Math4202_L11: "Topology II (Lecture 11)",
|
||||
Math4202_L12: "Topology II (Lecture 12)",
|
||||
Math4202_L13: "Topology II (Lecture 13)",
|
||||
}
|
||||
|
||||
131
content/Math4302/Math4302_L10.md
Normal file
131
content/Math4302/Math4302_L10.md
Normal file
@@ -0,0 +1,131 @@
|
||||
# Math4302 Modern Algebra (Lecture 10)
|
||||
|
||||
## Groups
|
||||
|
||||
### Group homomorphism
|
||||
|
||||
Recall the kernel of a group homomorphism is the set
|
||||
|
||||
$$
|
||||
\operatorname{ker}(\phi)=\{a\in G|\phi(a)=e'\}
|
||||
$$
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
Let $\phi:(\mathbb{Z},+)\to (\mathbb{Z}_n,+)$ where $\phi(k)=k\mod n$.
|
||||
|
||||
The kernel of $\phi$ is the set of all multiples of $n$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Theorem for one-to-one group homomorphism
|
||||
|
||||
$\phi:G\to G'$ is one-to-one if and only if $\operatorname{ker}(\phi)=\{e\}$
|
||||
|
||||
If $\phi$ is one-to-one, then $\phi(G)\leq G'$, $G$ is isomorphic ot $\phi(G)$ (onto automatically).
|
||||
|
||||
If $A$ is a set, then a permutation of $A$ is a bijection $f:A\to A$.
|
||||
|
||||
#### Cayley's Theorem
|
||||
|
||||
Every group $G$ is isomorphic to a subgroup of $S_A$ for some $A$ (and if $G$ is finite then $A$ can be taken to be finite.)
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
$D_n\leq S_n$, so $A=\{1,2,\cdots,n\}$
|
||||
|
||||
---
|
||||
|
||||
$\mathbb{Z}_n\leq S_n$, (use the set of rotations) so $A=\{1,2,\cdots,n\}$ $\phi(i)=\rho^i$ where $i\in \mathbb{Z}_n$ and $\rho\in D_n$
|
||||
|
||||
---
|
||||
|
||||
$GL(2,\mathbb{R})$. Set $A=\mathbb{R}^2$, for every $A\in GL(2,\mathbb{R})$, let $\phi(A)$ be the permutation of $\mathbb{R}^2$ induced by $A$, so $\phi(A)=f_A:\mathbb{R}^2\to \mathbb{R}^2$, $f_A(\begin{pmatrix}x\\y\end{pmatrix})=A\begin{pmatrix}x\\y\end{pmatrix}$
|
||||
|
||||
We want to show that this is a group homomorphism.
|
||||
|
||||
- $\phi(AB)=\phi(A)\phi(B)$ (it is a homomorphism)
|
||||
|
||||
$$
|
||||
\begin{aligned}
|
||||
f_{AB}(\begin{pmatrix}x\\y\end{pmatrix})&=AB\begin{pmatrix}x\\y\end{pmatrix}\\
|
||||
&=f_A(B\begin{pmatrix}x\\y\end{pmatrix})\\
|
||||
&=f_A(f_B(\begin{pmatrix}x\\y\end{pmatrix}))\\
|
||||
&=(f_A\circ f_B)(\begin{pmatrix}x\\y\end{pmatrix})\\
|
||||
\end{aligned}
|
||||
$$
|
||||
|
||||
- Then we need to show that $\phi$ is one-to-one.
|
||||
|
||||
It is sufficient to show that $\operatorname{ker}(\phi)=\{e\}$.
|
||||
|
||||
Solve $f_A(\begin{pmatrix}x\\y\end{pmatrix})=\begin{pmatrix}x\\y\end{pmatrix}$, the only choice for $A$ is the identity matrix.
|
||||
|
||||
Therefore $\operatorname{ker}(\phi)=\{e\}$.
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
<summary>Proof for Cayley's Theorem</summary>
|
||||
|
||||
Let $A=G$, for every $g\in G$, define $\lambda_g:G\to G$ by $\lambda_g(x)=gx$.
|
||||
|
||||
Then $\lambda_g$ is a **permutation** of $G$. (not homomorphism)
|
||||
|
||||
- $\lambda_g$ is one-to-one by cancellation on the left.
|
||||
- $\lambda_g$ is onto since $\lambda_g(g^{-1}y)=y$ for every $y\in G$.
|
||||
|
||||
We claim $\phi: G\to S_G$ define by $\phi(g)=\lambda_g$ is a group homomorphism that is one-to-one.
|
||||
|
||||
First we show that $\phi$ is homomorphism.
|
||||
|
||||
$\forall x\in G$
|
||||
|
||||
$$
|
||||
\begin{aligned}
|
||||
\phi(g_1)\phi(g_2)&=\lambda_{g_1}(\lambda_{g_2}(x))\\
|
||||
&=\lambda_{g_1g_2}(x)\\
|
||||
&=\phi(g_1g_2)x\\
|
||||
\end{aligned}
|
||||
$$
|
||||
|
||||
This is one to one since if $\phi(g_1)=\phi(g_2)$, then $\lambda_{g_1}=\lambda_{g_2}\forall x$, therefore $g_1=g_2$.
|
||||
|
||||
</details>
|
||||
|
||||
### Odd and even permutations
|
||||
|
||||
#### Definition of transposition
|
||||
|
||||
A $\sigma\in S_n$ is a transposition is a two cycle $\sigma=(i j)$
|
||||
|
||||
Fact: Every permutation in $S_n$ can be written as a product of transpositions. (may not be disjoint transpositions)
|
||||
|
||||
<details>
|
||||
<summary>Example of a product of transpositions</summary>
|
||||
|
||||
Consider $(1234)=(14)(13)(12)$.
|
||||
|
||||
In general, $(i_1,i_2,\cdots,i_m)=(i_1i_m)(i_2i_{m-1})(i_3i_{m-2})\cdots(i_1i_2)$
|
||||
|
||||
This is not the unique way.
|
||||
|
||||
$$
|
||||
(12)(34)=(42)(34)(23)(12)
|
||||
$$
|
||||
|
||||
</details>
|
||||
|
||||
But the parity of the number of transpositions is unique.
|
||||
|
||||
#### Theorem for parity of transpositions
|
||||
|
||||
If $\sigma\in S_n$ is written as a product of transposition, then the number of transpositions is either always odd or even.
|
||||
|
||||
#### Definition of odd and even permutations
|
||||
|
||||
$\sigma$ is an even permutation if the number of transpositions is even.
|
||||
|
||||
$\sigma$ is an odd permutation if the number of transpositions is odd.
|
||||
163
content/Math4302/Math4302_L11.md
Normal file
163
content/Math4302/Math4302_L11.md
Normal file
@@ -0,0 +1,163 @@
|
||||
# Math4302 Modern Algebra (Lecture 11)
|
||||
|
||||
## Groups
|
||||
|
||||
### Symmetric groups
|
||||
|
||||
#### Definition of odd and even permutations
|
||||
|
||||
$\sigma$ is an even permutation if the number of transpositions is even.
|
||||
|
||||
$\sigma$ is an odd permutation if the number of transpositions is odd.
|
||||
|
||||
#### Theorem for parity of transpositions
|
||||
|
||||
The parity of the number of transpositions is unique.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Prove using the determinant of a matrix, swapping the rows of the matrix multiply the determinant by $-1$.
|
||||
|
||||
Consider the identity matrix $I_n$. Then the determinant is $1$, let $(ij)A$, where $i\neq j$ denote the matrix obtained from $A$ by swapping the rows $j$ and $i$, then the determinant of $(1j)A$ is $-1$.
|
||||
|
||||
And,
|
||||
|
||||
$$
|
||||
\det((a_1b_1)(a_2b_2)\cdots(a_nb_n)A)=(-1)^n\det(A)
|
||||
$$
|
||||
|
||||
</details>
|
||||
|
||||
$S_3$ has 6 permutations $\{e,(12),(13),(23),(12)(23),(13)(23)\}$, 3 of them are even $\{e,(12)(23),(13)(23)\}$ and 3 of them are odd $\{(13),(12),(23)\}$.
|
||||
|
||||
#### Theorem for the number of odd and even permutations in symmetric groups
|
||||
|
||||
In general, $S_n$ has $n!$ permutations, half of them are even and half of them are odd.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Consider the set of odd permutations in $S_n$ and set of even permutations in $S_n$. Consider the function: $\alpha:S_n\to S_n$ where $\alpha(\sigma)=\sigma(12)$.
|
||||
|
||||
$\sigma$ is a bijection,
|
||||
|
||||
If $\sigma_1(12)=\sigma_2(12)$, then $\sigma_1=\sigma_2$.
|
||||
|
||||
If $\phi$ is an even permutation, $\alpha(\phi(12))=\phi(12)(12)=\phi$, therefore the number of elements in the set of odd and even permutations are the same.
|
||||
</details>
|
||||
|
||||
#### Definition for sign of permutations
|
||||
|
||||
For $\sigma\in S_n$, the sign of $\sigma$ is defined by $\operatorname{sign}(\sigma)=1$ if sigma is even and $-1$ if sigma is odd.
|
||||
|
||||
Then $\beta: S_n\to \{1,-1\}$ is a group under multiplication, where $\beta(\sigma)=\operatorname{sign}(\sigma)$.
|
||||
|
||||
Then $\beta$ is a group homomorphism.
|
||||
|
||||
#### Definition of alternating group
|
||||
|
||||
$\ker(\beta)\leq S_n$, and $\ker(\beta)$ is the set of even permutations. Therefore the set of even permutations is a subgroup of $S_n$. We denote as $A_n$ (also called alternating group).
|
||||
|
||||
and $|A_n|=\frac{n!}{2}$.
|
||||
|
||||
### Direct product of groups
|
||||
|
||||
#### Definition of direct product of groups
|
||||
|
||||
Let $G_1,G_2$ be two groups. Then the direct product of $G_1$ and $G_2$ is defined as
|
||||
|
||||
$$
|
||||
G_1\times G_2=\{(g_1,g_2):g_1\in G_1,g_2\in G_2\}
|
||||
$$
|
||||
|
||||
The operations are defined by $(a_1,b_1)*(a_2,b_2)=(a_1*a_2,b_1*b_2)$.
|
||||
|
||||
This group is well defined since:
|
||||
|
||||
The identity is $(e_1,e_2)$, where $e_1\in G_1$ and $e_2\in G_2$. (easy to verify)
|
||||
|
||||
The inverse is $(a_1,b_1)^{-1}=(a_1^{-1},b_1^{-1})$.
|
||||
|
||||
Associativity automatically holds by associativity of $G_1$ and $G_2$.
|
||||
|
||||
<details>
|
||||
<summary>Examples</summary>
|
||||
|
||||
Consider $\mathbb{Z}_\1\times \mathbb{Z}_2$.
|
||||
|
||||
$$
|
||||
\mathbb{Z}_\1\times \mathbb{Z}_2=\{(0,0),(0,1),(1,0),(1,1)\}
|
||||
$$
|
||||
|
||||
$(0,0)^2=(0,0)$, $(0,1)^2=(0,0)$, $(1,0)^2=(0,0)$, $(1,1)^2=(0,0)$
|
||||
|
||||
This is not a cyclic group, this is isomorphic to klein four group.
|
||||
|
||||
---
|
||||
|
||||
Consider $\mathbb{Z}_2\times \mathbb{Z}_3$.
|
||||
|
||||
$$
|
||||
\mathbb{Z}_2\times \mathbb{Z}_3=\{(0,0),(0,1),(0,2),(1,0),(1,1),(1,2),(2,0),(2,1),(2,2)\}
|
||||
$$
|
||||
|
||||
This is cyclic ((2,3) are coprime)
|
||||
|
||||
Consider:
|
||||
|
||||
$$
|
||||
\langle (1,1)\rangle=\{(0,0),(1,1),(0,2),(1,0),(0,1),(1,2)\}
|
||||
$$
|
||||
|
||||
</details>
|
||||
|
||||
#### Lemma for direct product of cyclic groups
|
||||
|
||||
$\mathbb{Z}_m\times \mathbb{Z}_n\simeq \mathbb{Z}_{mn}$ if and only if $m$ and $n$ have greatest common divisor $1$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
First assume $\operatorname{gcd}(m,n)=d>1$
|
||||
|
||||
Consider $(r,s)\in \mathbb{Z}_m\times \mathbb{Z}_n$.
|
||||
|
||||
We claim that order of $(r,s)$ is at most $\frac{mn}{d}<mn$.
|
||||
|
||||
Since $\frac{mn}{d}$ is integer, $\frac{mn}{d}=m_1dn_1$ where $m_1d$ is multiple of $m$ and $n_1d$ is multiple of $n$.
|
||||
|
||||
Therefore $r$ combine with itself $\frac{mn}{d}$ times is $0$ in $\mathbb{Z}_m$ and $s$ combine with itself $\frac{mn}{d}$ times is $0$ in $\mathbb{Z}_n$.
|
||||
|
||||
---
|
||||
|
||||
Other direction:
|
||||
|
||||
Assume $\operatorname{gcd}(m,n)=1$.
|
||||
|
||||
Claim order of $(1,1)=mn$, so $\mathbb{Z}_m\times \mathbb{Z}_n=\langle (1,1)\rangle$.
|
||||
|
||||
If $k$ is the order of $(1,1)$, then $k$ is a multiple of $m$ and a multiple of $n$.
|
||||
|
||||
</details>
|
||||
|
||||
Similarly, if $G_1,G_2,G_3,\ldots,G_k$ are groups, then
|
||||
|
||||
$$
|
||||
G_1\times G_2\times G_3\times \cdots\times G_k=\{(g_1,g_2,\ldots,g_k):g_1\in G_1,g_2\in G_2,\ldots,g_k\in G_k\}
|
||||
$$
|
||||
|
||||
is a group.
|
||||
|
||||
Easy to verify by associativity. $(G_1\times G_2)\times G_3=G_1\times G_2\times G_3$.
|
||||
|
||||
#### Some extra facts for direct product
|
||||
|
||||
1. $G_1\times G_2\simeq G_2\times G_1$, with $\phi(a_1,a_2)=(a_2,a_1)$.
|
||||
2. If $H_1\leq G_1$ and $H_2\leq G_2$, then $H_1\times H_2\leq G_1\times G_2$.
|
||||
|
||||
> [!WARNING]
|
||||
>
|
||||
> Not every subgroup of $G_1\times G_2$ is of the form $H_1\times H_2$.
|
||||
>
|
||||
> Consider $\mathbb{Z}_2\times \mathbb{Z}_2$ with subgroup $\{(0,0),(1,1)\}$, This forms a subgroup but not of the form $H_1\times H_2$.
|
||||
135
content/Math4302/Math4302_L12.md
Normal file
135
content/Math4302/Math4302_L12.md
Normal file
@@ -0,0 +1,135 @@
|
||||
# Math4303 Modern Algebra (Lecture 12)
|
||||
|
||||
## Groups
|
||||
|
||||
### Direct products
|
||||
|
||||
$\mathbb{Z}_m\times \mathbb{Z}_n$ is cyclic if and only if $m$ and $n$ have greatest common divisor $1$.
|
||||
|
||||
More generally, for $\mathbb{Z}_{n_1}\times \mathbb{Z}_{n_2}\times \cdots \times \mathbb{Z}_{n_k}$, if $n_1,n_2,\cdots,n_k$ are pairwise coprime, then the direct product is cyclic.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
For the forward direction, use $\mathbb{Z}_{n_1}\times \mathbb{Z}_{n_2}=\mathbb{Z}_{n_1n_2}$. if $n_1, n_2$ are coprime.
|
||||
|
||||
|
||||
For the backward, suppose to the contrary that for example $\gcd(n_1,n_2)=d>1$, then $G=\mathbb{Z}_{n_1}\times \mathbb{Z}_{n_2}\times H$, where any element in $H$ has order $\leq |H|$ and any element in $\mathbb{Z}_{n_1}\times \mathbb{Z}_{n_2}$ has order $<\frac{n_1n_2}{d}$, therefore, all the elements in $G$ will have order strictly less than the size $n_1n_2\ldots n_k$ of the group.
|
||||
|
||||
</details>
|
||||
|
||||
#### Corollary for composition of cyclic groups
|
||||
|
||||
If $n=p_1^{m_1}\ldots p_k^{m_k}$, where $p_i$ are distinct primes, then the group
|
||||
|
||||
$$
|
||||
G=\mathbb{Z}_n=\mathbb{Z}_{p_1^{m_1}}\times \mathbb{Z}_{p_2^{m_2}}\times \cdots \times \mathbb{Z}_{p_k^{m_k}}
|
||||
$$
|
||||
|
||||
is cyclic.
|
||||
|
||||
<details>
|
||||
<summary>Example for product of cyclic groups and order of element</summary>
|
||||
|
||||
$$
|
||||
\mathbb{Z}_{8}\times\mathbb{Z}_8\times \mathbb{Z}_12
|
||||
$$
|
||||
|
||||
the order for $(1,1,1)$ is 24.
|
||||
|
||||
What is the maximum order of an element in this group?
|
||||
|
||||
Guess:
|
||||
|
||||
$8*3=24$
|
||||
|
||||
</details>
|
||||
|
||||
### Structure of finitely generated abelian groups
|
||||
|
||||
#### Theorem for finitely generated abelian groups
|
||||
|
||||
Every finitely generated abelian group $G$ is isomorphic to
|
||||
|
||||
$$
|
||||
Z_{p_1}^{n_1}\times Z_{p_2}^{n_2}\times \cdots \times Z_{p_k}^{n_k}\times\underbrace{\mathbb{Z}\times \ldots \times \mathbb{Z}}_{m\text{ times}}
|
||||
$$
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
If $G$ is abelian of size $8$, then $G$ is isomorphic to one of the following:
|
||||
|
||||
- $\mathbb{Z}_2\times \mathbb{Z}_2\times \mathbb{Z}_2$ (non cyclic)
|
||||
- $\mathbb{Z}_2\times \mathbb{Z}_4$ (non cyclic)
|
||||
- $\mathbb{Z}_2$ (cyclic)
|
||||
|
||||
And any two of them are not isomorphic
|
||||
|
||||
---
|
||||
|
||||
Find all abelian group of order $72$.
|
||||
|
||||
Since $72=2^3*3^2$, There are 3 possibilities for the $2^3$ part, and there are 2 possibilities for the $3^2$ part.
|
||||
|
||||
Note that $\mathbb{Z}_8\times\mathbb{Z}_9$, where $8,9$ are coprime, $\mathbb{Z}_8\times\mathbb{Z}_9=\mathbb{Z}_{72}$, is cyclic.
|
||||
|
||||
There are 6 possibilities in total.
|
||||
|
||||
</details>
|
||||
|
||||
#### Corollary for divisor size of abelian subgroup
|
||||
|
||||
If $g$ is abelian and $|G|=n$, then for every divisor $m$ of $n$, $G$ has a subgroup of order $m$.
|
||||
|
||||
> [!WARNING]
|
||||
>
|
||||
> This is not true if $G$ is not abelian.
|
||||
>
|
||||
> Consider $A_4$ (alternating group for $S_4$) does not have a subgroup of order 6.
|
||||
|
||||
|
||||
<details>
|
||||
<summary>Proof for the corollary</summary>
|
||||
|
||||
Write $G=\mathbb{Z}_{p_1}^{n_1}\times \mathbb{Z}_{p_2}^{n_2}\times \cdots \times \mathbb{Z}_{p_k}^{n_k}$ where $p_i$ are distinct primes.
|
||||
|
||||
Therefore $n=p_1^{m_1}\ldots p_k^{m_k}$.
|
||||
|
||||
For any divisor $d$ of $n$, we can write $d=p_1^{m_1}\ldots p_k^{m_k}$, where $m_i\leq n_i$.
|
||||
|
||||
Now for each $p_i$, we choose the subgroup $H_i$ of size $p_i^{m_i}$ in $\mathbb{Z}_{p_i}^{n_i}$. (recall that every cyclic group of size $r$ and any divisor $s$ of $r$, there is a subgroup of order $s$. If the group is generated by $a$, then use $a^{\frac{r}{s}}$ to generate the subgroup.)
|
||||
|
||||
We can construct the subgroup $H=H_1\times H_2\times \cdots \times H_k$ is the subgroup of $G$ of order $d$.
|
||||
</details>
|
||||
|
||||
### Cosets
|
||||
|
||||
#### Definition of Cosets
|
||||
|
||||
Let $G$ be a group and $H$ its subgroup.
|
||||
|
||||
Define a relation on $G$ and $a\sim b$ if $a^{-1}b\in H$.
|
||||
|
||||
This is an equivalence relation.
|
||||
|
||||
- Reflexive: $a\sim a$: $a^{-1}a=e\in H$
|
||||
- Symmetric: $a\sim b\Rightarrow b\sim a$: $a^{-1}b\in H$, $(a^{-1}b)^{-1}=b^{-1}a\in H$
|
||||
- Transitive: $a\sim b$ and $b\sim c\Rightarrow a\sim c$ : $a^{-1}b\in H, b^{-1}c\in H$, therefore their product is also in $H$, $(a^{-1}b)(b^{-1}c)=a^{-1}c\in H$
|
||||
|
||||
So we get a partition of $G$ to equivalence classes.
|
||||
|
||||
Let $a\in G$, the equivalence class containing $a$
|
||||
|
||||
$$
|
||||
aH=\{x\in G| a\sim x\}=\{x\in G| a^{-1}x\in H\}=\{x|x=ah\text{ for some }h\in H\}
|
||||
$$
|
||||
|
||||
This is called the coset of $a$ in $H$.
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
Consider $G=S_3$
|
||||
|
||||
</details>
|
||||
143
content/Math4302/Math4302_L13.md
Normal file
143
content/Math4302/Math4302_L13.md
Normal file
@@ -0,0 +1,143 @@
|
||||
# Math4302 Modern Algebra (Lecture 13)
|
||||
|
||||
## Groups
|
||||
|
||||
### Cosets
|
||||
|
||||
Last time we see that (left coset) $a\sim b$ (to differentiate from right coset, we may denote it as $a\sim_L b$) by $a^{-1}b\in H$ defines an equivalence relation.
|
||||
|
||||
#### Definition of Equivalence Class
|
||||
|
||||
Let $a\in H$, and the equivalence class containing $a$ is defined as:
|
||||
|
||||
$$
|
||||
aH=\{x|a\simeq x\}=\{x|a^{-1}x\in H\}=\{x|x=ah\text{ for some }h\in H\}
|
||||
$$.
|
||||
|
||||
#### Properties of Equivalence Class
|
||||
|
||||
$aH=bH$ if and only if $a\sim b$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
If $aH=bH$, then since $a\in aH, a\in bH$, then for some $h$, $a=bh$, since $b^{-1}a\in H$, so $a^{-1}b\in H$, therefore $a\simeq b$.
|
||||
|
||||
If $a\sim b$, then $aH\subseteq bH$, since anything in $aH$ is related to $a$, therefore it is related to $b$ so $a\in bH$.
|
||||
|
||||
$bH\subseteq aH$, apply the reflexive property for equivalence relation, therefore $b\in aH$.
|
||||
|
||||
So $aH=bH$.
|
||||
|
||||
</details>
|
||||
|
||||
If $aH\cap bH\neq \emptyset$, then $aH=bH$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
If $x\in aH\cap bH$, then $x\sim a$ and $x\sim b$, so $a\sim b$, so $aH=bH$.
|
||||
|
||||
</details>
|
||||
|
||||
$aH=H$ if and only if $a\in H$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
$aH=eH$ if and only if $a\sim e$, if and only if $a\in H$.
|
||||
|
||||
</details>
|
||||
|
||||
$aH$ is called **left coset** of $a$ in $H$.
|
||||
|
||||
<details>
|
||||
<summary>Examples</summary>
|
||||
|
||||
Consider $G=S_3=\{e,\rho,\rho^2,\tau_1,\tau_2,\tau_3\}$.
|
||||
|
||||
where $\rho=(123),\rho^2=(132),\tau_1=(12),\tau_2=(23),\tau_3=(13)$.
|
||||
|
||||
$H=\{e,\rho,\rho^2\}$.
|
||||
|
||||
All the left coset for $H$ is $H=eH=\rho H=\rho^2H$.
|
||||
|
||||
$$
|
||||
\tau_1\rho=(23)=\tau_2\\
|
||||
\tau_1\rho^2=(13)=\tau_3\\
|
||||
\tau_2\rho=(31)=\tau_3\\
|
||||
\tau_2\rho^2=(12)=\tau_1
|
||||
\tau_3\rho=(12)=\tau_1\\
|
||||
\tau_3\rho^2=(23)=\tau_2
|
||||
$$
|
||||
|
||||
$$
|
||||
\tau_1H=\{\tau_1,\tau_2,\tau_3\}=\tau_2H=\tau_3H\\
|
||||
$$
|
||||
|
||||
---
|
||||
|
||||
Consider $G=\mathbb{Z}$ with $H=5\mathbb{Z}$.
|
||||
|
||||
We have 5 cosets, $H,1+H,2+H,3+H,4+H$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Lemma for size of cosets
|
||||
|
||||
Any coset of $H$ has the same cardinality as $H$.
|
||||
|
||||
Define $\phi:H\to aH$ by $\phi(h)=ah$.
|
||||
|
||||
$\phi$ is an bijection, if $ah=ah'\implies h=h'$, it is onto by definition of $aH$.
|
||||
|
||||
#### Corollary: Lagrange's Theorem
|
||||
|
||||
If $G$ is a finite group, and $H\leq G$, then $|H|\big\vert |G|$. (size of $H$ divides size of $G$)
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Suppose $H$ has $r$ distinct cosets, then $|G|=r|H|$, so $|H|$ divides $|G|$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Corollary for Lagrange's Theorem
|
||||
|
||||
If $|G|=p$, where $p$ is a prime number, then $G$ is cyclic.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Prick $e\neq a\in G$, let $H=\langle a\rangle \leq G$, then $|H|$ divides $|G|$, since $p$ is prime, then $|H|=|G|$, so $G=\langle a \rangle$.
|
||||
|
||||
</details>
|
||||
|
||||
If $G$ is finite and $a\in G$, then $\operatorname{ord}(a)\big\vert|G|$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Since $\operatorname{ord}(a)=|\langle a\rangle|$, and $\langle a\rangle $ is a subgroup, so $\operatorname{ord}(a)\big\vert|G|$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Definition of index
|
||||
|
||||
Suppose $H\leq G$, the number of distinct left cosets of $H$ is called the index of $H$ in $G$. Notation is $(G:H)$.
|
||||
|
||||
#### Definition of right coset
|
||||
|
||||
Suppose $H\leq G$, define the equivalence relation by $a\sim 'b$ (or $a\sim_R b$ in some textbook) if $a b^{-1}\in H$. (note the in left coset, we use $a^{-1}b \in H$, or equivalently $b^{-1}a \in H$, these are different equivalence relations)
|
||||
|
||||
The equivalent class is defined
|
||||
|
||||
$$
|
||||
Ha=\{x\in G|x\sim'a\}=\{x\in G|xa^{-1}\in H\}=\{x|x=ha\text{ for some }h\in H\}
|
||||
$$
|
||||
|
||||
Some properties are the same as the left coset
|
||||
|
||||
- $Ha=H\iff a\in H$
|
||||
- $Ha=Hb$ if and only if $a\sim'b\iff a b^{-1}\in H$.
|
||||
- $Ha\cap Hb\neq \emptyset\iff Ha=Hb$.
|
||||
|
||||
Some exercises: Find all the left and right cosets of $G=S_3$, there should be 2 left cosets and 2 right cosets (giving different partition of $G$).
|
||||
133
content/Math4302/Math4302_L4.md
Normal file
133
content/Math4302/Math4302_L4.md
Normal file
@@ -0,0 +1,133 @@
|
||||
# Math4302 Modern Algebra (Lecture 4)
|
||||
|
||||
## Groups
|
||||
|
||||
### Group Isomorphism
|
||||
|
||||
#### Definition of isomorphism
|
||||
|
||||
Let $(G_1,*_1)$ and $(G_2,*_2)$ be two groups. Then $(G_1,*_1)$ and $(G_2,*_2)$ are isomorphic if there exists a bijection $f:G_1\to G_2$ such that for all $x,y\in G_1$, $f(x*y)=f(x)*f(y)$. We say that $(G_1,*_1)$ is isomorphic to $(G_2,*_2)$.
|
||||
|
||||
$$
|
||||
(G_1,*_1)\simeq (G_2,*_2)
|
||||
$$
|
||||
|
||||
<details>
|
||||
<summary>Example and non-example for isomorphism</summary>
|
||||
|
||||
As we have seen in class, $(\mathbb{Z}_4,+)$ and $(\{1,-1,i,-i\},*)$ are isomorphic.
|
||||
|
||||
---
|
||||
|
||||
$(\mathbb{Z},+)$ and $(\mathbb{R},+)$ are not isomorphic. There is no bijection from $(\mathbb{Z},+)$ to $(\mathbb{R},+)$.
|
||||
|
||||
---
|
||||
|
||||
Let $M_2(\mathbb{R})$ denotes the set of $2\times 2$ matrices with addition. Then $(\mathbb{R}^4,+)$ and $(M_2(\mathbb{R}),+)$ are isomorphic.
|
||||
|
||||
---
|
||||
|
||||
$(\mathbb{Z},+)$ and $(\mathbb{Q},+)$ are not isomorphic.
|
||||
|
||||
- There exists bijection mapping $\mathbb{Z}\to \mathbb{Q}$, but
|
||||
|
||||
Suppose we have $f(1)=a\in \mathbb{Q}$, so there exists unique element $f(x), x\in \mathbb{Z}$ such that $f(x)=\frac{a}{2}$, if such function $f$ is isomorphic (preserves addition), then $f(2x)=f(x)+f(x)=a$. So $2x=1$, such $x$ does not exist in $\mathbb{Z}$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Isomorphism of Groups defines an equivalence relation
|
||||
|
||||
Isomorphism of groups is an equivalence relation.
|
||||
|
||||
1. Reflexive: $(G_1,*_1)\simeq (G_1,*_1)$
|
||||
2. Symmetric: $(G_1,*_1)\simeq (G_2,*_2)\implies (G_2,*_2)\simeq (G_1,*_1)$
|
||||
3. Transitive: $(G_1,*_1)\simeq (G_2,*_2)\land (G_2,*_2)\simeq (G_3,*_3)\implies (G_1,*_1)\simeq (G_3,*_3)$
|
||||
|
||||
Easy to prove using bijective maps and definition of isomorphism.
|
||||
|
||||
#### Some fun facts
|
||||
|
||||
<!-- Up to isomorphism, there is only one group of order $m$ for any $m\in\mathbb{N}$. That is $(\mathbb{Z}_m,+)$. -->
|
||||
|
||||
For any prime number, there is only one group of order $p$ for any $p\in\mathbb{N}$.
|
||||
|
||||
[OEIS A000001](https://oeis.org/A000001)
|
||||
|
||||
#### Example of non-abelian finite groups
|
||||
|
||||
Permutations (Symmetric groups) $S_n$.
|
||||
|
||||
Let $A$ be a set of $n$ elements, a permutation of $A$ is a bijection from $A$ to $A$.
|
||||
|
||||
$\sigma: A\to A$
|
||||
|
||||
Let $A$ be a finite set, $A=\{1,2,...,n\}$. Then there are $n!$ permutations of $A$.
|
||||
|
||||
We can denote each permutation on $A=\{1,2,...,n\}$ by
|
||||
|
||||
$$
|
||||
\sigma=\begin{pmatrix}
|
||||
1&2&...&n\\
|
||||
\sigma(1)&\sigma(2)&...&\sigma(n)
|
||||
\end{pmatrix}
|
||||
$$
|
||||
|
||||
#### Symmetric Groups
|
||||
|
||||
The set of permutation on a set $A$ form a group under function composition.
|
||||
|
||||
- Identity: $\sigma_{id}=\begin{pmatrix}
|
||||
1&2&...&n\\
|
||||
1&2&...&n
|
||||
\end{pmatrix}$
|
||||
- Inversion: If $f: A\to A$ is a bijection, then $f^{-1}: A\to A$ is a bijection and is the inverse of $f$.
|
||||
- Associativity: $(\sigma_1*\sigma_2)*\sigma_3=\sigma_1*(\sigma_2*\sigma_3)$
|
||||
|
||||
$|S_n|=n!$
|
||||
|
||||
When $n=1,2$, the group is abelian.
|
||||
|
||||
but when $n=3$, we have some $\sigma,\tau\in S_3$ such that $\sigma*\tau\neq \tau*\sigma$.
|
||||
|
||||
Let $\sigma=\begin{pmatrix}
|
||||
1&2&3\\
|
||||
2&3&1
|
||||
\end{pmatrix}$ and $\tau=\begin{pmatrix}
|
||||
1&2&3\\
|
||||
3&2&1\\
|
||||
\end{pmatrix}$, then $\sigma*\tau=\begin{pmatrix}
|
||||
1&2&3\\
|
||||
1&3&2
|
||||
\end{pmatrix}$ and $\tau*\sigma=\begin{pmatrix}
|
||||
1&2&3\\
|
||||
2&1&3
|
||||
\end{pmatrix}$.
|
||||
|
||||
Therefore $\tau*\sigma\neq \sigma*\tau$.
|
||||
|
||||
Then we have a group of order $3!=6$ that is not abelian.
|
||||
|
||||
For any $n\geq 3$, $S_n$ is not abelian. (Proof by induction, keep $\sigma,\tau$ extra entries being the same$).
|
||||
|
||||
Another notation for permutations is using the cycle.
|
||||
|
||||
Suppose we have $\sigma=\begin{pmatrix}
|
||||
1&2&3&4\\
|
||||
2&3&1&4\\
|
||||
\end{pmatrix}$, then we have the cycle $(1,2,3)(4)$.
|
||||
|
||||
this means we send $1\to 2\to 3\to 1$ and $4\to 4$.
|
||||
|
||||
Some case we ignore $(4)$ and just write $(1,2,3)$.
|
||||
|
||||
> [!TIP]
|
||||
>
|
||||
> From now on, we use $G$ to denote $(G,*)$ and $ab$ to denote $a*b$ to save chalks.
|
||||
>
|
||||
> If $G$ is abelian, we use $+$ to denote the group operations
|
||||
>
|
||||
> - Instead of $a*b$ or $ab$, we write $a+b$.
|
||||
> - Instead of $a^{-1}$, we write $-a$.
|
||||
> - Instead of $e$, we write $0$.
|
||||
> - Instead of $a^{n}$, we write $na$.
|
||||
|
||||
106
content/Math4302/Math4302_L5.md
Normal file
106
content/Math4302/Math4302_L5.md
Normal file
@@ -0,0 +1,106 @@
|
||||
# Math4302 Modern Algebra (Lecture 5)
|
||||
|
||||
## Groups
|
||||
|
||||
### Subgroups
|
||||
|
||||
A subset $H\subseteq G$ is a subgroup of $G$ if
|
||||
|
||||
- $e\in H$
|
||||
- $\forall a,b\in H, a b\in H$
|
||||
- $a\in H\implies a^{-1}\in H$
|
||||
|
||||
_$H$ with $*$ is a group_
|
||||
|
||||
We denote as $H\leq G$.
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
For an arbitrary group $(G,*)$,
|
||||
|
||||
$(\{e\},*)$ and $(G,*)$ are always subgroups.
|
||||
|
||||
---
|
||||
|
||||
$(\mathbb{Z},+)$ is a subgroup of $(\mathbb{R},+)$.
|
||||
|
||||
---
|
||||
|
||||
Non-example:
|
||||
|
||||
$(\mathbb{Z}_+,+)$ is not a subgroup of $(\mathbb{Z},+)$.
|
||||
|
||||
---
|
||||
|
||||
Subgroup of $\mathbb{Z}_4$:
|
||||
|
||||
$(\{0,1,2,3\},+)$ (if $1\in H$, $3\in H$)
|
||||
|
||||
$(\{0,2\},+)$
|
||||
|
||||
$(\{0\},+)$
|
||||
|
||||
---
|
||||
|
||||
Subgroup of $\mathbb{Z}_5$:
|
||||
|
||||
$(\{0,1,2,3,4\},+)$
|
||||
|
||||
$(\{0\},+)$
|
||||
|
||||
_Cyclic group with prime order has only two subgroups_
|
||||
|
||||
---
|
||||
|
||||
Let $D_n$ denote the group of symmetries of a regular $n$-gon. (keep adjacent points pairs).
|
||||
|
||||
$$
|
||||
D_n=\{\sigma\in S_n\mid i,j\text{ are adjacent } \iff \sigma(i),\sigma(j)\text{ are adjacent }\}
|
||||
$$
|
||||
|
||||
$$
|
||||
\begin{pmatrix}
|
||||
1&2&3&4\\
|
||||
2&3&1&4
|
||||
\end{pmatrix}\notin D_4
|
||||
$$
|
||||
|
||||
$D_4$ has order $8$ and $S_4$ has order $24$.
|
||||
|
||||
$|D_n|=2n$. ($n$ option to rotation, $n$ option to reflection. For $\sigma(1)$ we have $n$ option, $\sigma(2)$ has 2 option where the remaining only has 1 option.)
|
||||
|
||||
Since $1-4$ is not adjacent in such permutation.
|
||||
|
||||
$D_n\leq S_n$ ($S_n$ is the symmetric group of $n$ elements).
|
||||
|
||||
</details>
|
||||
|
||||
#### Lemma of subgroups
|
||||
|
||||
If $H\subseteq G$ is a non-empty subset of a group $G$.
|
||||
|
||||
then ($H$ is a subgroup of $G$) if and only if ($a,b\in H\implies ab^-1\in H$).
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
If $H$ is subgroup, then $e\in H$, so $H$ is non-empty and if $a,b\in H$, then $b^{-1}\in H$, so $ab^{-1}\in H$.
|
||||
|
||||
---
|
||||
|
||||
If $H$ has the given property, then $H$ is non-empty and if $a,b\in H$, then $ab^-1\in H$, so
|
||||
|
||||
- There is some $a,a\in H$, $aa^{-1}\in H$, so $e\in H$.
|
||||
- If $b\in H$, then $e\in H$, so $eb^{-1}\in H$, so $b^{-1}\in H$.
|
||||
- If $b,c\in H$, then $c^{-1}$, so $bc^{-1}^{-1}\in H$, so $bc\in H$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Cyclic group
|
||||
|
||||
$G$ is cyclic if $G$ is a subgroup generated by $a\in G$. (may be infinite)
|
||||
|
||||
$\mathbb{Z}_n\leq D_n\leq S_n$.
|
||||
|
||||
Cyclic group is always abelian.
|
||||
149
content/Math4302/Math4302_L6.md
Normal file
149
content/Math4302/Math4302_L6.md
Normal file
@@ -0,0 +1,149 @@
|
||||
# Math4302 Modern Algebra (Lecture 6)
|
||||
|
||||
## Subgroups
|
||||
|
||||
### Dihedral group
|
||||
|
||||
The dihedral group $D_n$ is the group of all rotations and reflections about the center of the regular polygon of $n$ sides.
|
||||
|
||||
$|S_n|=n!, |D_n|=2n$
|
||||
|
||||
### Cyclic group
|
||||
|
||||
$G=\langle a\rangle=\{1,a,a^2,\cdots\}$ for some $a\in G$
|
||||
|
||||
<details>
|
||||
<summary>Example of cyclic group</summary>
|
||||
|
||||
$(\mathbb{Z}_n,+)$ is cyclic and $\mathbb{Z}_n=\langle 1\rangle=\{0,1,2,\cdots,n-1\}$
|
||||
|
||||
---
|
||||
|
||||
$(\mathbb{Z},+)$ is cyclic and $\mathbb{Z}=\langle 1\rangle=\langle -1 \rangle$
|
||||
|
||||
---
|
||||
|
||||
$S_3$ is not cyclic
|
||||
|
||||
$\langle e\rangle=\{e\}$
|
||||
$\langle (1,2)\rangle=\{e,(1,2)\}$
|
||||
$\langle (1,3)\rangle=\{e,(1,3)\}$
|
||||
$\langle (2,3)\rangle=\{e,(2,3)\}$
|
||||
$\langle (1,2,3)\rangle=\{e,(1,2,3),(1,3,2)\}$
|
||||
$\langle (1,3,2)\rangle=\{e,(1,3,2),(1,2,3)\}$
|
||||
|
||||
</details>
|
||||
|
||||
#### Every cyclic group is abelian
|
||||
|
||||
Every cyclic group is abelian
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Let $G=\langle a\rangle$ be a cyclic group, then $\forall g_1,g_2\in G$ we have $g_1g_2=g_2g_1$ since $g_1g_2=a^k_1a^k_2=a^{k_1+k_2}$ and $g_2g_1=a^k_2a^k_1=a^{k_1+k_2}$
|
||||
|
||||
</details>
|
||||
|
||||
#### Definition for order of element
|
||||
|
||||
Let $G$ be a group, then the order of $g\in G$ is defined to be the size of the smallest subgroup containing $g$.
|
||||
|
||||
If $|\langle g\rangle|$ is infinite, then we say that $g$ has infinite order.
|
||||
|
||||
<details>
|
||||
<summary>Example of order of element</summary>
|
||||
|
||||
$5$ in $(\mathbb{Z},+)$ has infinite order.
|
||||
|
||||
---
|
||||
|
||||
$5$ in $(\mathbb{Z}_{10},+)$ has order $2$.
|
||||
|
||||
$\langle 5\rangle=\{0,5\}$.
|
||||
|
||||
---
|
||||
|
||||
$5$ in $(\mathbb{Z}_{6},+)$ has order $6$.
|
||||
|
||||
$\langle 5\rangle=\{0,5,4,3,2,1\}$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Lemma for order of element
|
||||
|
||||
Let $G$ be a group, then $a\in G$ has order $n$ if $n$ is the smallest positive integer such that $a^n=e$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
There are 2 cases:
|
||||
|
||||
Case 1:
|
||||
|
||||
There is no positive $n$ such that $a^n=e$.
|
||||
|
||||
Then $a^i\neq a^j$ if $i\neq j, i,j\in \mathbb{N}$.
|
||||
|
||||
Reason: if $a^i=a^j$, then $a^{i-j}=e$.
|
||||
|
||||
Then the order of group is infinite.
|
||||
|
||||
Case 2:
|
||||
|
||||
There is a positive $n$ such that $a^n=e$.
|
||||
|
||||
Let $n$ be the smallest such positive integer. Then we claim $\langle a^n\rangle=\{e,a^1,a^2,\cdots,a^{n-1}\}$.
|
||||
|
||||
We claim they are all distinct.
|
||||
|
||||
Suppose not, then we can have $a^i=a^j$ for $i\neq j$, $0\leq i,j\leq n-1$.
|
||||
|
||||
Then $a^{i-j}=e$ but $i-j\leq n-1$. Therefore $n$ is not the smallest positive integer such that $a^n=e$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Theorem for cyclic group up to isomorphism
|
||||
|
||||
Suppose $G$ is a cyclic group,
|
||||
|
||||
- If $|G|=n$, then $|G|\simeq \mathbb{Z}_n^+$
|
||||
- If $|G|=\infty$, then $|G|\simeq \mathbb{Z}$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Case 1:
|
||||
|
||||
If $|G|=\infty$, then we can map $G$ to $(\mathbb{Z},+)$, where $G=\langle a\rangle$. $\phi(n)=a^n$. This gives a bijection between $G$ and $(\mathbb{Z},+)$.
|
||||
|
||||
where $\phi(n+m)=a^{n+m}=a^n a^m=\phi(n)\phi(m)$.
|
||||
|
||||
Case 2:
|
||||
|
||||
If $|G|=n$, then we can map $G$ to $(\mathbb{Z}_n,+)$, where $G=\langle a\rangle$. $\phi(n)=a^n$. This gives a bijection between $G$ and $(\mathbb{Z}_n,+)$.
|
||||
|
||||
where $\phi(n+m)=\phi(r)=a^{n+m}=a^n a^m=\phi(n)\phi(m)$.
|
||||
</details>
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
Let $H=\langle (12)(345)\rangle\subseteq S_5$. Then $H\simeq \mathbb{Z}_6^+$.
|
||||
|
||||
Let $\tau=(12)(345)$
|
||||
|
||||
All the elements of $H$ are:
|
||||
|
||||
- $\tau^0=(12)(345)$
|
||||
- $\tau^1=(453)$
|
||||
- $\tau^2=(12)(534)$
|
||||
- $\tau^3=(345)$
|
||||
- $\tau^4=(12)(453)$
|
||||
- $\tau^5=(534)$
|
||||
|
||||
</details>
|
||||
|
||||
#### GCD and order
|
||||
|
||||
If $G=\langle a\rangle$, then $H=\langle a^k\rangle$, $|H|=\frac{n}{d}$ where $d=\operatorname{gcd}(n,k)$.
|
||||
83
content/Math4302/Math4302_L7.md
Normal file
83
content/Math4302/Math4302_L7.md
Normal file
@@ -0,0 +1,83 @@
|
||||
# Math4302 Modern Algebra (Lecture 7)
|
||||
|
||||
## Subgroups
|
||||
|
||||
### Cyclic group
|
||||
|
||||
Last time, let $G$ be a group and $a\in G$. $|\langle a\rangle|=$ smallest positive $n$ such that $a^n=e$.
|
||||
|
||||
$\langle a\rangle=\{a^0,a^1,a^2,\cdots,a^{n-1}\}$.
|
||||
|
||||
|
||||
#### Lemma subgroup of cyclic group is cyclic
|
||||
|
||||
Every subgroup of a cyclic group is cyclic.
|
||||
|
||||
$G=\langle a\rangle$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Let $H\leq G$ be a subgroup.
|
||||
|
||||
If $H=\{e\}$, we are done.
|
||||
|
||||
Otherwise, let $m$ be the smallest positive integer such that $a^m\in H$. We claim $H=\langle a^m\rangle$.
|
||||
|
||||
- $\langle a^m\rangle\subseteq H$. trivial since $a^m\in H$ and $H$ is a subgroup.
|
||||
- $H\subseteq\langle a^m\rangle$. Suppose $a^k\in H$, need to show $a^k\in \langle a^m\rangle$
|
||||
Divide $k$ by $m$: $k=qm+r$, $0\leq r\leq m-1$, Then $a^k\in H\implies a^{qm+r}\in H$. Also $a^m\in H$, then $(a^m)^q\in H$, so $a^mq\in H$, $a^-mq\in H$, so $a^{k}a^{-mq}\in H$, so $a^r\in H$, so $r$ has to be zero.
|
||||
By our choice of $m$, $k=mq$, so $a^k=a^mq\in \langle a^m\rangle$.
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
Every subgroup of $(\mathbb{Z},+)$ is of the form
|
||||
|
||||
like the multiples of $n$: $n\mathbb{Z}=\langle n\rangle$ for some $n\geq 0$.
|
||||
|
||||
In particular, if $n,m\geq 1$ are in $\mathbb{Z}$, then the subgroup $\{nr+ms|r,s\in \mathbb{Z}\}\leq \mathbb{Z}$.
|
||||
|
||||
is equal to $d\mathbb{Z}$ where $d=\operatorname{gcd}(n,m)$.
|
||||
|
||||
</details>
|
||||
|
||||
Skip $\operatorname{gcd}$ part, check for Math 4111 notes in this site.
|
||||
|
||||
|
||||
#### Lemma for size of cyclic subgroup
|
||||
|
||||
Let $G=\langle a\rangle$, $|G|=n$, and $H=\langle a^m\rangle\subseteq G$. Then $|H|=\frac{n}{d}$ where $d=\operatorname{gcd}(|G|,|H|)$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Recall $|H|$ is the smallest power of $a^m$ which is equal to $e$.
|
||||
|
||||
Let $d=\operatorname{gcd}(m,n)$, so $m=m_1d$, $n=n_1d$. and $\frac{n}{\operatorname{gcd}(m,n)}=n_1$,
|
||||
|
||||
- $(a^m)^{n_1}=a^{mn_1}=a^{m_1dn_1}=a^{m_1n}=(a^n)^{m_1}=e$.
|
||||
- If $(a^m)^k=e$, the $a^{mk}=e\implies$ $mk$ is a multiple of $n$,
|
||||
- If $a^\ell=e$, divide $\ell$ by $n$, $\ell=nq+r$, $0\leq r\leq n-1$, then $e=a^\ell=a^{nq+r}=a^r$, $r$ has to be zero, so $a^\ell=a^r=e$. $n|\ell$.
|
||||
- $n_1d|m_1dk$, but by the definition of smallest common divisor, $m_1,n_1$ should not have common divisor other than $1$. So $n_1|m_1k$, $n_1|k\implies k\geq n_1$.
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
<summary>Example Applying the lemma</summary>
|
||||
|
||||
Let $G=\langle a \rangle$, $|G|=6$, $H=\langle a^4\rangle$. Then $|H|=\frac{6}{d}=3$ where $d=\operatorname{gcd}(6,4)=2$.
|
||||
|
||||
To check this we do enumeration $\langle a^4\rangle=\{e,a^4,a^2\}$.
|
||||
|
||||
---
|
||||
|
||||
Find generator of $\mathbb{Z}_9$:
|
||||
|
||||
Using the coprime, we have $g=\{1,2,4,5,7,8\}$.
|
||||
|
||||
</details>
|
||||
|
||||
Corollary: $\langle a^m\rangle=G\iff |H|=n\iff \frac{n}{d}=n\iff \operatorname{gcd}(m,n)=1$ $m,n$ are coprime.
|
||||
146
content/Math4302/Math4302_L8.md
Normal file
146
content/Math4302/Math4302_L8.md
Normal file
@@ -0,0 +1,146 @@
|
||||
# Math4302 Modern Algebra (Lecture 8)
|
||||
|
||||
## Subgroups
|
||||
|
||||
### Cyclic group
|
||||
|
||||
#### Subgroup of cyclic group is cyclic
|
||||
|
||||
Every subgroup of a cyclic group is cyclic.
|
||||
|
||||
#### Order of subgroup of cyclic group
|
||||
|
||||
If $a\in G$ and $|\langle a\rangle|$ be the smallest positive $n$ such that $a^n=e$, then $\langle a\rangle=\{e,a,a^2,\cdots,a^{n-1}\}$ and $a^{m_1}=a^{m_2}\iff m_1=m_2\mod n$. ($n$ divides $m_1-m_2$)
|
||||
|
||||
#### Size of subgroup of cyclic group
|
||||
|
||||
Let $G=\langle a\rangle$ and $H=\langle a^m\rangle$. Then $|H|=\frac{|G|}{d}$ where $d=\operatorname{gcd}(|G|,|H|)$. In particular, $\langle a^m\rangle=G\iff \operatorname{gcd}(n,m)=1$.
|
||||
|
||||
#### GCD decides the size of subgroup
|
||||
|
||||
Suppose $G=\langle a\rangle$, $|G|=n$.
|
||||
|
||||
Then $\langle a^{m_1}\rangle=\langle a^{m_2}\rangle\iff \operatorname{gcd}(n,m_2)=\operatorname{gcd}(n,m_1)$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
$\implies$:
|
||||
|
||||
$\langle a^{m_1}\rangle=\langle a^{m_2}\rangle\implies \operatorname{gcd}(n,m_1)=\operatorname{gcd}(n,m_2)$
|
||||
|
||||
$\impliedby$:
|
||||
|
||||
Suppose $d=\operatorname{gcd}(n,m_1)=\operatorname{gcd}(n,m_2)$.
|
||||
|
||||
Enough to show $a^{m_1}\in \langle a^{m_2}\rangle$. (then we conclude $\langle a^{m_1}\rangle=\langle a^{m_2}\rangle$ and by symmetry $\langle a^{m_2}\rangle=\langle a^{m_1}\rangle$.)
|
||||
|
||||
Equivalent to show that $a^{m_1}=(a^{m_2})^k$ for some integer $k$. That is $n$ divides $m_1-km_2$ for some $k\in \mathbb{Z}$.
|
||||
|
||||
From last lecture, we know that $d$ can be written as $d=nr+m_2 s$ for some $r,s\in \mathbb{Z}$.
|
||||
|
||||
Multiply by $\frac{m_1}{d}$, (since $d$ divides $m_1$, this is an integer).
|
||||
|
||||
So $m_1=nr\frac{m_1}{d}+m_2s\frac{m_1}{d}$.
|
||||
|
||||
Therefore $n$ divides $m_1-(\frac{m_1}{d}s)m_2$, so $k=\frac{m_1}{d}s$. works.
|
||||
|
||||
</details>
|
||||
|
||||
#### Corollaries for subgroup of cyclic group
|
||||
|
||||
Let $G=\langle a\rangle$ be a cyclic group of finite order.
|
||||
|
||||
1. If $H\leq G$, then $|H|$ is a divisor of $|G|$. (More generally true for finite groups.)
|
||||
2. For any $d$ divides $|G|$, there is exactly one subgroup of $G$ of order $d$. $\langle a^m\rangle$ where $m=\frac{|G|}{d}$.
|
||||
|
||||
<details>
|
||||
<summary>Examples</summary>
|
||||
|
||||
$(\mathbb{Z}_18,+)$.
|
||||
|
||||
The subgroup with size $6$ is $\langle 3\rangle=\{0,3,6,9,12,15\}=\langle 15\rangle$.
|
||||
|
||||
Note that $\operatorname{gcd}(18,3)=3=\operatorname{gcd}(18,15)$.
|
||||
|
||||
$\langle 6\rangle=\{0,6,12\}$.
|
||||
|
||||
$\langle 9\rangle=\{0,9\}$.
|
||||
|
||||
$\langle 2\rangle=\{0,2,4,6,8,10,12,14,16\}$ (generators are $2,4,8,10,14,16$ since they have gcd $2$ with $18$).
|
||||
|
||||
</details>
|
||||
|
||||
### Non-cyclic groups
|
||||
|
||||
Let $G$ be a group and $a,b\in G$, then we use $\langle a,b\rangle$ to mean the subgroup of $G$ generated by combination of $a$ and $b$.
|
||||
|
||||
$$
|
||||
\langle a,b\rangle\coloneqq \{e,a,b,ab,ba,a^{-1},b^{-1},(ab)^{-1},(ba)^{-1},\ldots\}
|
||||
$$
|
||||
|
||||
This is a subgroup of $G$ since it is closed and $e=a^0$.
|
||||
|
||||
#### Klein 4 group
|
||||
|
||||
Klein 4 group is abelian but not cyclic.
|
||||
|
||||
|*|e|a|b|c|
|
||||
|--|---|---|---|---|
|
||||
|e|e|a|b|c|
|
||||
|a|a|e|c|b|
|
||||
|b|b|c|e|a|
|
||||
|c|c|b|a|e|
|
||||
|
||||
The subgroups are
|
||||
|
||||
$\langle e\rangle=\{e\}$
|
||||
|
||||
$\langle a\rangle=\{e,a\}$
|
||||
|
||||
$\langle b\rangle=\{e,b\}$
|
||||
|
||||
$\langle c\rangle=\{e,c\}$
|
||||
|
||||
Therefore $G$ is **not cyclic** and **not isomorphic** to $\mathbb{Z}_4$.
|
||||
|
||||
Here $G=\langle a,b\rangle=\{e,a,b,ab=c\}$.
|
||||
|
||||
More generally, if we have $a_i\in G$, where $i\in I$, then $\langle a_i,i\in I\rangle=$ all possible combinations of $a_i$ with their inverses. Is a subgroup of $G$.
|
||||
|
||||
Another way to describe is that $\langle a_i,i\in I\rangle=\bigcap_{H\leq G, a_i\in H,i\in I}H$.
|
||||
|
||||
#### Definition of finitely generated group
|
||||
|
||||
If $G$ is a group and if there is a finite set $a_1,\ldots, a_n\in G$ such that $G=\langle a_1,\ldots, a_n\rangle$, then $G$ is called finitely generated.
|
||||
|
||||
<details>
|
||||
<summary>Examples</summary>
|
||||
|
||||
Any finite group is finitely generated.
|
||||
|
||||
---
|
||||
|
||||
$(\mathbb{Q},+)$ is not finitely generated.
|
||||
|
||||
Suppose for the contrary, there is a finite set $\frac{a_1}{b_1},\ldots,\frac{a_n}{b_n}\in \mathbb{Q}$ such that
|
||||
|
||||
$$
|
||||
\mathbb{Q}=\langle \frac{a_1}{b_1},\ldots,\frac{a_n}{b_n}\rangle=\{t_1\frac{a_1}{b_1},\ldots,t_n\frac{a_n}{b_n}|t_1,t_2,\ldots,t_n\in \mathbb{Z}\}
|
||||
$$.
|
||||
|
||||
Pick prime $p$ such that $p>|b_1|,\ldots,|b_n|$. Then $\frac{1}{p}\in \mathbb{Q}$.
|
||||
|
||||
$$
|
||||
\frac{1}{p}=t_1\frac{a_1}{b_1}+t_2\frac{a_2}{b_2}+\cdots+t_n\frac{a_n}{b_n}=\frac{A}{b_1b_2\cdots b_n}
|
||||
$$
|
||||
|
||||
This implies that $pA=b_1b_2\cdots b_n$.
|
||||
|
||||
Since $p$ is prime, $p|b_i$ for some $i$.
|
||||
|
||||
However, by our construction, $p>|b_i|$ and cannot divide $b_i$.
|
||||
|
||||
Contradiction.
|
||||
|
||||
</details>
|
||||
138
content/Math4302/Math4302_L9.md
Normal file
138
content/Math4302/Math4302_L9.md
Normal file
@@ -0,0 +1,138 @@
|
||||
# Math4302 Modern Algebra (Lecture 9)
|
||||
|
||||
## Groups
|
||||
|
||||
### Non-cyclic groups
|
||||
|
||||
#### Dihedral groups
|
||||
|
||||
The dihedral group $D_n$ is the group of symmetries of a regular $n$-gon.
|
||||
|
||||
(Permutation that sends adjacent vertices to adjacent vertices)
|
||||
|
||||
$D_n<S_n$
|
||||
|
||||
$|S_n|=n!, |D_n|=2n$
|
||||
|
||||
We can classify dihedral groups as follows:
|
||||
|
||||
$\rho \in D_n$ as the rotation of a regular $n$-gon by $\frac{2\pi}{n}$.
|
||||
|
||||
$\phi\in D_n$ as a reflection of a regular $n$-gon with respect to $x$-axis.
|
||||
|
||||
We can enumerate the elements of $D_n$ as follows:
|
||||
|
||||
$$
|
||||
D_n=\langle \phi,\rho\rangle=\{e,\rho,\rho^2,\cdots,\rho^{n-1},\phi,\phi\rho,\phi\rho^2,\cdots,\phi\rho^{n-1}\}
|
||||
$$
|
||||
|
||||
We claim these elements are all distinct.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
Consider the first half, clearly $\rho_i\neq \rho_j$ if $0\leq i<j\leq n-1$.
|
||||
|
||||
Also $\phi\rho_i\neq \phi\rho_j$ if $0\leq i<j\leq n-1$. otherwise $\rho_i=\rho_j$
|
||||
|
||||
Also $\rho^i\neq \rho^j\phi$ where $0\leq i,j\leq n-1$.
|
||||
|
||||
Otherwise $\rho^{i-j}=\phi$, but reflection (with some point fixed) cannot be any rotation (no points are fixed).
|
||||
|
||||
</details>
|
||||
|
||||
In $D_n$, $\phi\rho=\rho^{n-1}\phi$, more generally, $\phi\rho^i=\rho^{n-i}\phi$ for any $i\in\mathbb{Z}$.
|
||||
|
||||
### Group homomorphism
|
||||
|
||||
#### Definition for group homomorphism
|
||||
|
||||
Let $G,G'$ be groups.
|
||||
|
||||
$\phi:G\to G'$ is called a group homomorphism if $\phi(g_1g_2)=\phi(g_1)\phi(g_2)$ for all $g_1,g_2\in G$ (Note that $\phi$ may not be bijective).
|
||||
|
||||
This is a weaker condition than isomorphism.
|
||||
|
||||
<details>
|
||||
<summary>Example</summary>
|
||||
|
||||
$GL(2,\mathbb{R})=\{A\in M_{2\times 2}(\mathbb{R})|det(A)\neq 0\}$
|
||||
|
||||
Then $\phi:GL(2,\mathbb{R})\to (\mathbb{R}-\{0\},\cdot)$ where $\phi(A)=\det(A)$ is a group homomorphism, since $\det(AB)=\det(A)\det(B)$.
|
||||
|
||||
This is not one-to-one but onto, therefore not an isomorphism.
|
||||
|
||||
---
|
||||
|
||||
$(\mathbb{Z}_n,+)$ and $D_n$ has homomorphism $(\mathbb{Z}_n,+)\to D_n$ where $\phi(k)=\rho^k$
|
||||
|
||||
$\phi(i+j)=\rho^{i+j\mod n}=\rho^i\rho^j=\phi(i)+\phi(j)$.
|
||||
|
||||
This is not onto but one-to-one, therefore not an isomorphism.
|
||||
|
||||
---
|
||||
|
||||
Let $G,G'$ be two groups, let $e$ be the identity of $G$ and let $e'$ be the identity of $G'$.
|
||||
|
||||
Let $\phi:G\to G'$, $\phi(a)=e'$ for all $a\in G$.
|
||||
|
||||
This is a group homomorphism,
|
||||
|
||||
$$
|
||||
\phi(ab)=\phi(a)\phi(b)=e'e'=e'
|
||||
$$
|
||||
|
||||
This is generally not onto and not one-to-one, therefore not an isomorphism.
|
||||
|
||||
</details>
|
||||
|
||||
#### Corollary for group homomorphism
|
||||
|
||||
Let $G,G'$ be groups and $\phi:G\to G'$ be a group homomorphism. $e$ is the identity of $G$ and $e'$ is the identity of $G'$.
|
||||
|
||||
1. $\phi(e)=e'$
|
||||
2. $\phi(a^{-1})=(\phi(a))^{-1}$ for all $a\in G$
|
||||
3. If $H\leq G$, then $\phi(H)\leq G'$, where $\phi(H)=\{\phi(a)|a\in H\}$.
|
||||
4. If $K\leq G'$ then $\phi^{-1}(K)\leq G$, where $\phi^{-1}(K)=\{a\in G|\phi(a)\in K\}$.
|
||||
|
||||
<details>
|
||||
<summary>Proof</summary>
|
||||
|
||||
(1) $\phi(e)=e'$
|
||||
|
||||
Consider $\phi(ee)=\phi(e)\phi(e)$, therefore $\phi(e)=e'$ by cancellation on the left.
|
||||
|
||||
---
|
||||
|
||||
(2) $\phi(a^{-1})=(\phi(a))^{-1}$
|
||||
|
||||
Consider $\phi(a^{-1}a)=\phi(a^{-1})\phi(a)=\phi(e)$, therefore $\phi(a^{-1})$ is the inverse of $\phi(a)$ in $G'$.
|
||||
|
||||
---
|
||||
|
||||
(3) If $H\leq G$, then $\phi(H)\leq G'$, where $\phi(H)=\{\phi(a)|a\in H\}$.
|
||||
|
||||
- $e\in H$ implies that $e'=\phi(e)\in\phi(H)$.
|
||||
- If $x\in \phi(H)$, then $x=\phi(a)$ for some $a\in H$. So $x^{-1}=(\phi(x))^{-1}=\phi(x^{-1})\in\phi(H)$. But $x\in H$, so $x^{-1}\in H$, therefore $x^{-1}\in\phi(H)$.
|
||||
- If $x,y\in \phi(H)$, then $x,y=\phi(a),\phi(b)$ for some $a,b\in H$. So $xy=\phi(a)\phi(b)=\phi(ab)\in\phi(H)$ (by homomorphism). Since $ab\in H$, $xy\in\phi(H)$.
|
||||
|
||||
---
|
||||
|
||||
(4) If $K\leq G'$ then $\phi^{-1}(K)\leq G$, where $\phi^{-1}(K)=\{a\in G|\phi(a)\in K\}$.
|
||||
|
||||
- $e'\in K$ implies that $e=\phi^{-1}(e')\in\phi^{-1}(K)$.
|
||||
- If $x\in \phi^{-1}(K)$, then $x=\phi(a)$ for some $a\in G$. So $x^{-1}=(\phi(x))^{-1}=\phi(x^{-1})\in\phi^{-1}(K)$. But $x\in G$, so $x^{-1}\in G$, therefore $x^{-1}\in\phi^{-1}(K)$.
|
||||
- If $x,y\in \phi^{-1}(K)$, then $x,y=\phi(a),\phi(b)$ for some $a,b\in G$. So $xy=\phi(a)\phi(b)=\phi(ab)\in\phi^{-1}(K)$ (by homomorphism). Since $ab\in G$, $xy\in\phi^{-1}(K)$.
|
||||
|
||||
</details>
|
||||
|
||||
#### Definition for kernel and image of a group homomorphism
|
||||
|
||||
Let $G,G'$ be groups and $\phi:G\to G'$ be a group homomorphism.
|
||||
|
||||
$\operatorname{ker}(\phi)=\{a\in G|\phi(a)=e'\}=\phi^{-1}(\{e'\})$ is called the kernel of $\phi$.
|
||||
|
||||
Facts:
|
||||
|
||||
- $\operatorname{ker}(\phi)$ is a subgroup of $G$. (proof by previous corollary (4))
|
||||
- $\phi$ is onto if and only if $\operatorname{ker}(\phi)=\{e\}$ (the trivial subgroup of $G$). (proof forward, by definition of one-to-one; backward, if $\phi(a)=\phi(b)$, then $\phi(a)\phi(b)^{-1}=e'$, so $\phi(a)\phi(b^{-1})=e'$, so $ab^{-1}=e$, so $a,b=e$, so $a=b$)
|
||||
@@ -6,4 +6,14 @@ export default {
|
||||
Math4302_L1: "Modern Algebra (Lecture 1)",
|
||||
Math4302_L2: "Modern Algebra (Lecture 2)",
|
||||
Math4302_L3: "Modern Algebra (Lecture 3)",
|
||||
Math4302_L4: "Modern Algebra (Lecture 4)",
|
||||
Math4302_L5: "Modern Algebra (Lecture 5)",
|
||||
Math4302_L6: "Modern Algebra (Lecture 6)",
|
||||
Math4302_L7: "Modern Algebra (Lecture 7)",
|
||||
Math4302_L8: "Modern Algebra (Lecture 8)",
|
||||
Math4302_L9: "Modern Algebra (Lecture 9)",
|
||||
Math4302_L10: "Modern Algebra (Lecture 10)",
|
||||
Math4302_L11: "Modern Algebra (Lecture 11)",
|
||||
Math4302_L12: "Modern Algebra (Lecture 12)",
|
||||
Math4302_L13: "Modern Algebra (Lecture 13)",
|
||||
}
|
||||
|
||||
@@ -1,7 +1,7 @@
|
||||
# Welcome to NoteNextra
|
||||
|
||||
> [!WARNING]
|
||||
><!-- > This site use [Algolia Search](https://www.algolia.com/) to search the content. However, due to some unknown reasons, when the index page is loaded, the search bar is calling default PageFind package from Nextra. **If you find the search bar is not working**, please try to redirect to another page and then back to the index page or search in another page. -->
|
||||
> This site use [Algolia Search](https://www.algolia.com/) to search the content. Index updated on weekly basis, the search result may be delayed. For latest search, please use github document search if possible.
|
||||
>
|
||||
> This site use SSG to generate the static pages. And cache is stored to your browser, this may not reveal the latest updates. **If you find some notes are not shown on sidebar but the class already ends more than 24 hours**, please try to access the page directly via the URL, or force reload the cache (for example, change the URL to `.../Math4201/Math4201_L{number}` to access the note of the lecture `Math4201_L{number}` and then refresh the page).
|
||||
|
||||
@@ -13,7 +13,7 @@ The primary audience of this project is for those challenge takers who are takin
|
||||
|
||||
So here it is. A lite server for you to read my notes.
|
||||
|
||||
**Remember, I take notes don't means that I like them and paying attention to the lecture.**
|
||||
**Remember, I take notes don't means that I like them and paying attention to the lectures.**
|
||||
|
||||
<p style="color: red; font-weight: bold">It's because I'm too easy to fall asleep if I stop doing something on my hand when my mind is wandering.</p>
|
||||
|
||||
|
||||
BIN
public/CSE4303/Network-data-formats.png
Normal file
BIN
public/CSE4303/Network-data-formats.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 39 KiB |
BIN
public/CSE4303/TCP-protocal-stack.png
Normal file
BIN
public/CSE4303/TCP-protocal-stack.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 29 KiB |
Reference in New Issue
Block a user